Wintapix Malicious Driver
Overview
Wintapix Driver is a malicious driver that was operating about three years ago but just caught the eyes of the hunters a little while ago.
It’s primarily targeting saudi arabia as a large number of the samples found were there and also in the middle east.
the operator behind it is not specifically known, but from the targets and TTPs, there is a thought that they are Iranian threat actors.
Technical Analysis
The first thing to look at any Driver is whether it’s signed or not, and in our case, the driver is not signed which means it may be used in the post-exploitation part of the kill chain to achieve more persistence and being more stealthy.
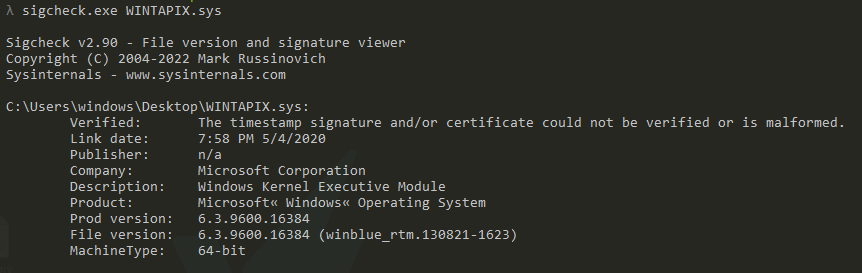
The sample looks a bit obfuscated at the DrivrEntry function which makes it a little hard to trace what’s the sequential flow of the driver statically So I decided to start looking at the functions found in the driver to construct a view of the capabilities of the driver especially because the number of functions is not that much.
Capabilities
Code Injection
The driver has the capability to inject code into running processes but it has some conditions the process must meet.
The first one is the process shouldn’t be one of these processes.
- wininit.exe
- csrss.exe
- smss.exe
- services.exe
- winlogon.exe
- lsass.exe
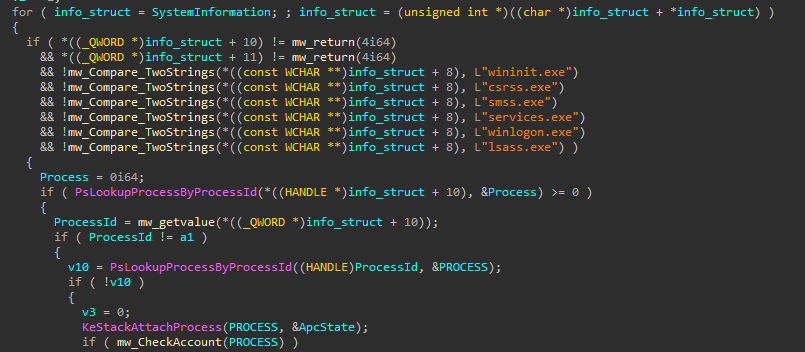
The second one is that the process should be running with local system user
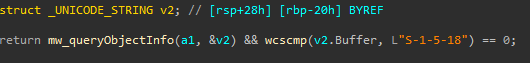
The shell Code that will be injected is left unpacked inside the Driver’s memory.
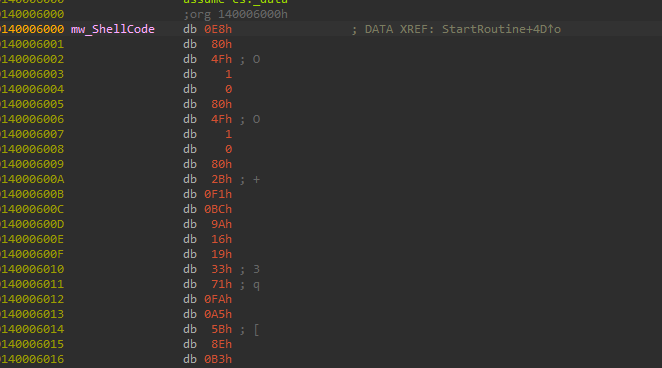
Registry persistence
The Driver also adds an entry to itself into the service registry key.
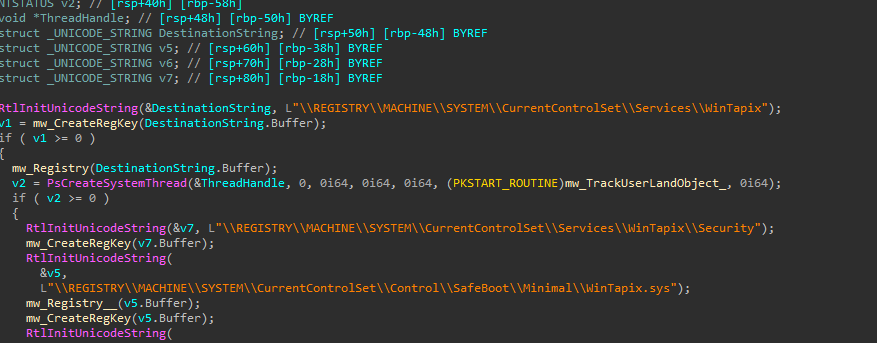
Defeat Deletion
The Driver registers a handle to an event to notify if any changes happen to the directory where he lives, To be able to write itself back if deleted.
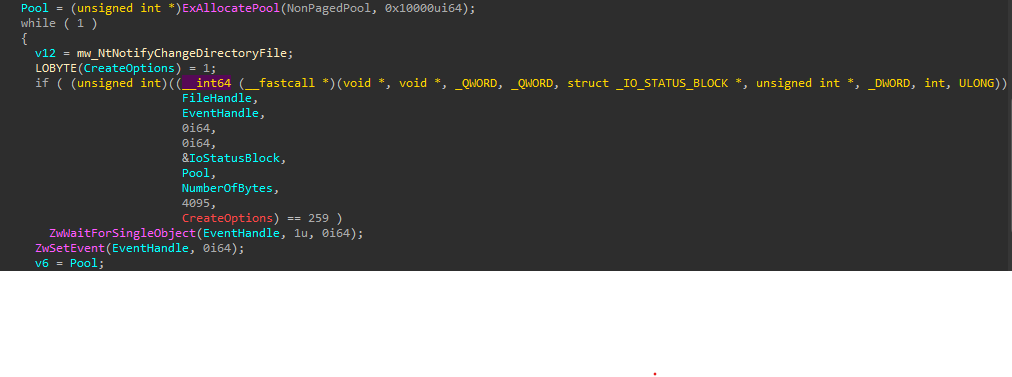
Kernel Debugging
Now It’s time for the underground world kernel to debug the Driver.
I will not go throw how to set up your own kernel Debugging Environment, It’s mentioned everywhere and I will get you a link to one of them in the resources Section.
all I will do to start is set up a breakpoint at the nt!IopLoadDriver function and then load my driver then start it, this will trigger our breakpoint before the DriverEntry.
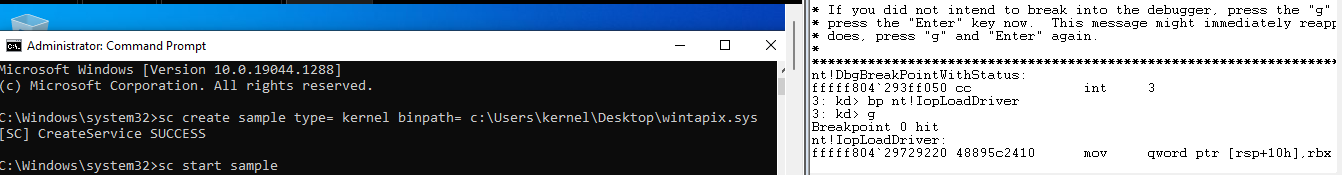
You will land in a big function so we need to see only the call instructions inside it using the command.
uf /c @rip
We are interested in PnpCallDriverEntry function that will lead us to our Driver Entry.
Doing the same inside this function we look for nt!guard_dispatch_icall then inside it, you will find a call to register rax that holds the Entry of your Driver.
(look at the resources for detailed info about this lookup process)
Now we are inside our DriverEntry.
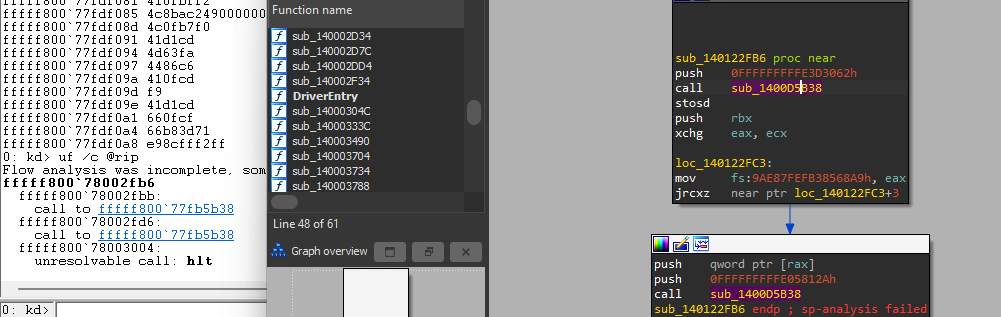
As the sample uses VMProtect which is a very complicated anti-analysis packer and I already got what I wanted from the static analysis, I will continue my investigation with the shell code that will be injected.
Shell Code Analysis
After extracting the shell code out of the Driver and uploading it to VirusTotal, It got detected as a Donut Shell Code.
Donut is a position-independent code that enables in-memory execution of VBScript, JScript, EXE, DLL files, and dotNET assemblies”. It can take any of the supported executable formats and convert them into Position-Independent Code (PIC).
which also can be identified with the human eye by looking at the first few bites.
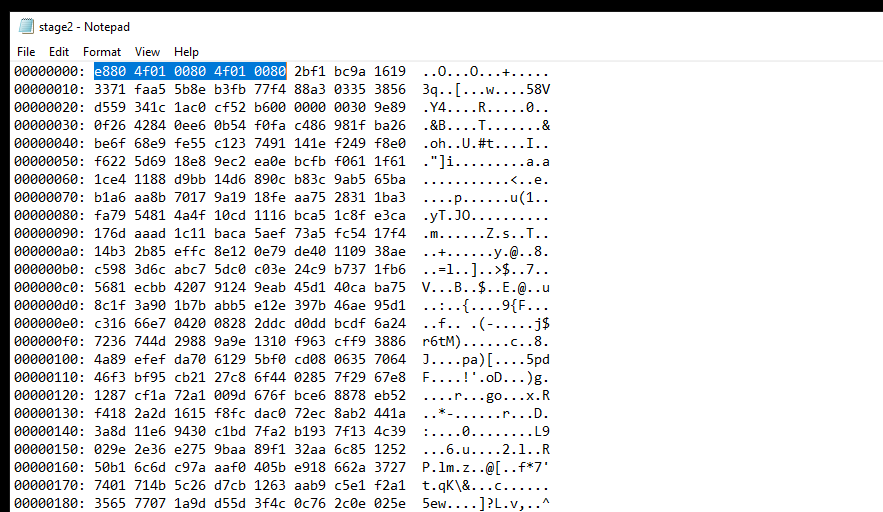
As the shell code will start by call (E8) and the next word repeated twice(in our case 4f01 0080 4f01 0080), here is also a yara rule that detects it.
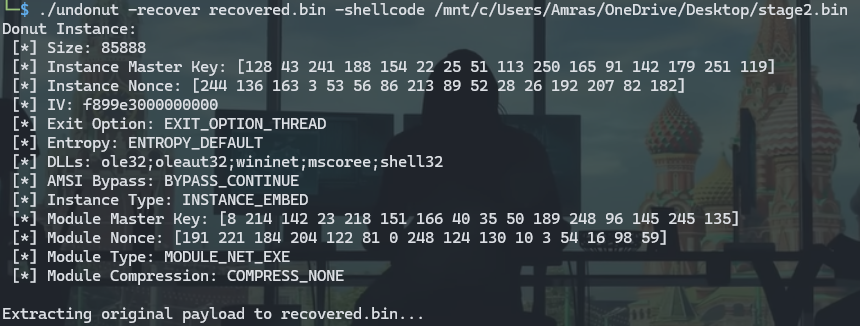
We can get the original file and reverse this code change using this tool undonut.
Stage 2
The malware starts by decrypting values from resources and saving the decrypted data in two arrays.
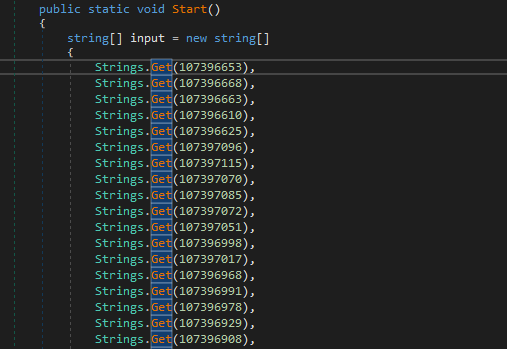
These are some of the decrypted values.
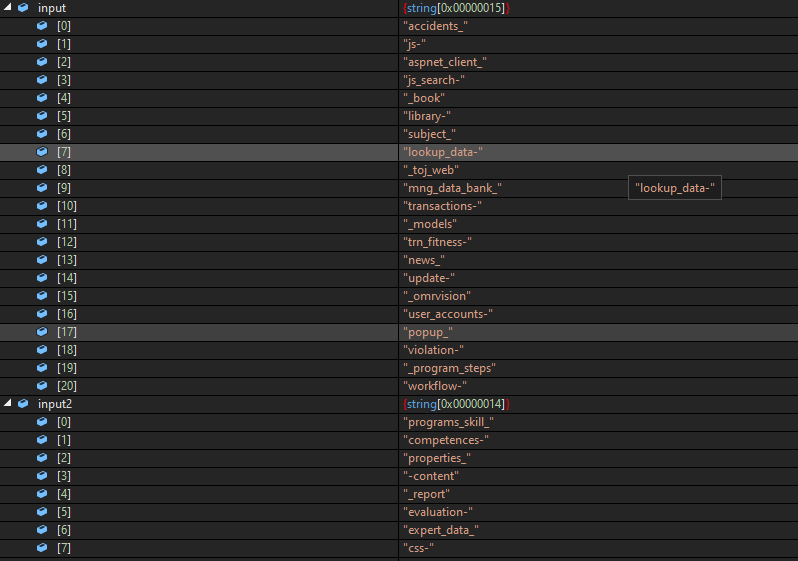
I found then that these strings are used as endpoint names in a web server to be accessed by the threat actor to achieve his goal.
there are two uses for this endpoint will be taking advantage of
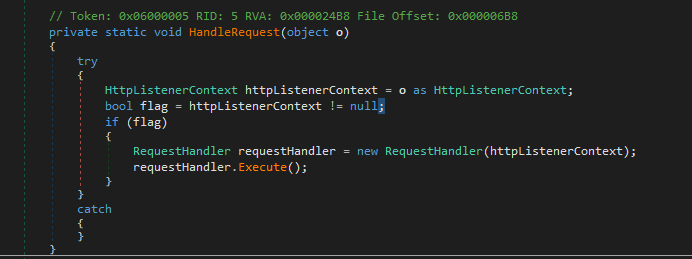
- Backdoor
- Proxy
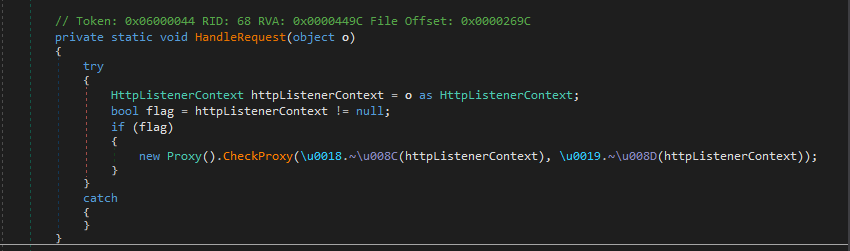
The malware also has the ability to terminate services like the logging service from the server.
Yara Rule
rule WINTAPIX : rootkit
{
meta:
description = "Detection Rule for WINTAPIX Rootkit"
email = "amr.ashraf.re@outlook.com"
author = "Amr Ashraf"
strings:
$mz = {4D 5A} // MZ header
$string1 = "\\SystemRoot\\System32\\drivers\\WinTapix.sys" wide
$string2 = "S-1-5-18" wide
$string3 = "wininit.exe" wide
$string4 = "csrss.exe" wide
$string5 = "smss.exe" wide
$string6 = "services.exe" wide
$string7 = "winlogon.exe" wide
$string8 = "lsass.exe" wide
$shellcode = {E8 80 4F 01 00 80 4F 01 00 80 2B F1 BC 9A 16 19 33 71 FA A5 5B 8E B3 FB 77 F4 88 A3 03 35 38 56 D5 59 34 1C 1A C0 CF 52 B6 00 00 00 00 30 9E 89}
condition:
($mz at 0) and
(all of ($string*) or $shellcode)
}
hashes
WINTAPIX : 8578bff36e3b02cc71495b647db88c67c3c5ca710b5a2bd539148550595d0330
.Net payload : 786298c0d98aaf35777738a43a41546c6c8b1972b9bd601fb6cccf2c8f539ae4
Ida Database
https://github.com/amr-git-dot/amr-git-dot.github.io/blob/main/assets/database/ida_database.7z
Resources
https://www.fortinet.com/blog/threat-research/wintapix-kernal-driver-middle-east-countries https://www.triplefault.io/2017/07/setting-up-kernel-debugging-using.html https://blogg.pwc.no/styringogkontroll/starting-dynamic-analysis-on-a-windows-x64-rootkit