CrowdStrike abuse campaign
OverView
Everyone knows about the global outage on Windows Systems that happened because of the failure on one of CrowdStrike kernel modules, and we all expected attackers to misuser this for their benefit.
The Delivery of this malware that we are going to discuss here depends on sending an email containing a Compressed file attachment which contains an update instruction that instructs the user to execute an executable file.
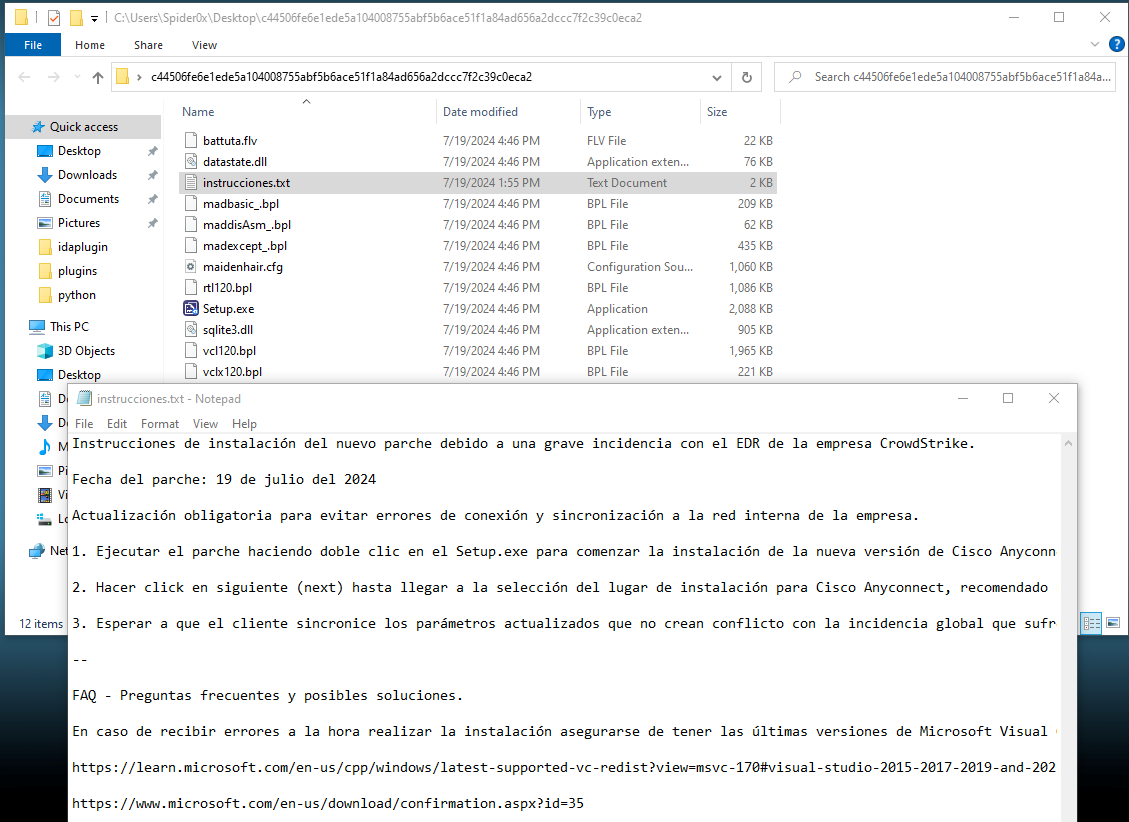
We can also find that the ZIP file contains multiple files with the executable itself, so let’s get into the starting point the attacker wanted to execute and construct the malware functionality from there.
Sample info
SHA256: 5ae3838d77c2102766538f783d0a4b4205e7d2cdba4e0ad2ab332dc8ab32fea9
the file has a high entropy in multiple sections which indicates that it may be obfuscated.
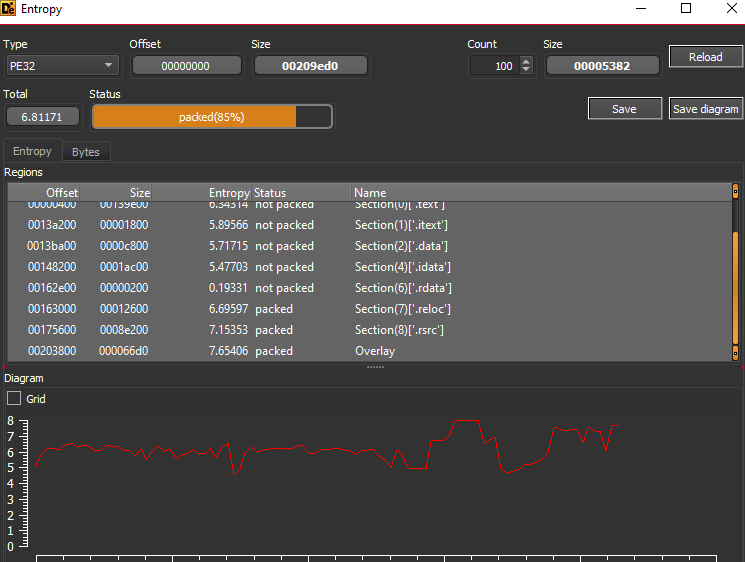
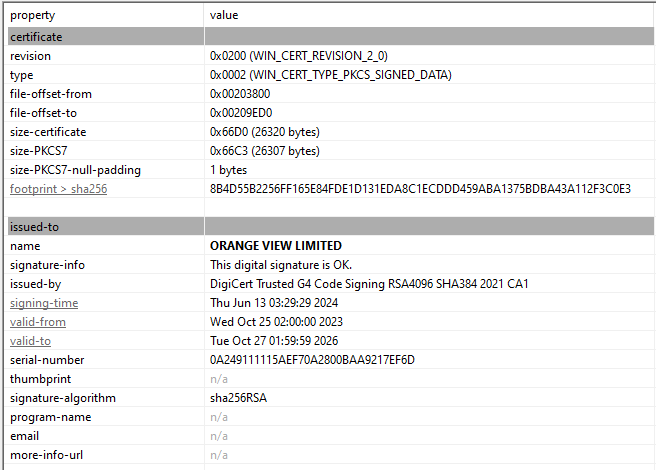
Interestingly we can find that the file is signed with a valid certificate.
Also, we can notice that when uploading the executable to a Sandbox service like “Triage”, it didn’t manage to observe malicious functionality.
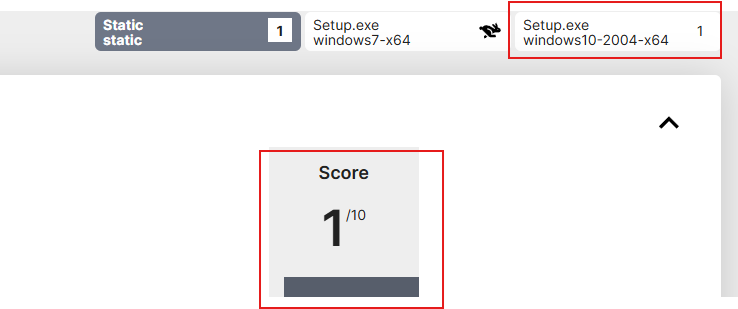
this could be due to the malware depending on the other files that come with it, or it has an anti-analysis technique that managed to bypass the sandbox defenses.
Behavioral And Code Analysis
Now, we can try behavioral analysis on our machine after failing to get results behaviorally from Sandbox, we can do that by running the sample and monitoring our environment using tools like, “DirWatch, Sysmon, Procmon, Fakenet”
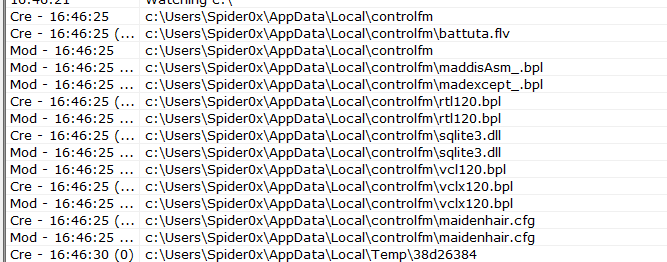
From there, we can notice some actions, we can notice coping the files with the malware on the downloaded ZIP file to another location in the AppData folder.
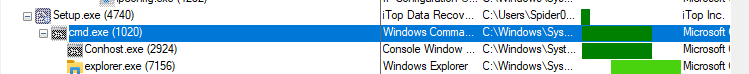
Also, We can notice spawning child processes like “cmd” and “explorer.
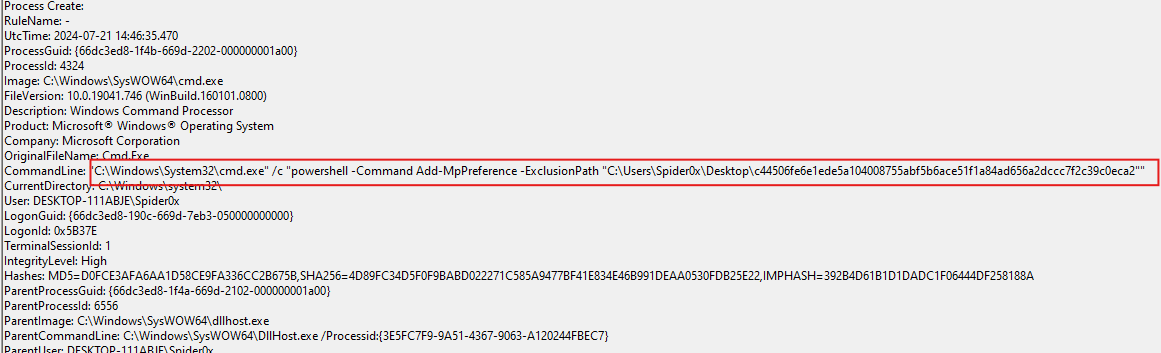
From Sysmon, we can find interesting functionalities, we can find the malware adds exclusion to its directory from Windows Defender.
We can see the creation of an LNK file in the Startup folder for persistence.
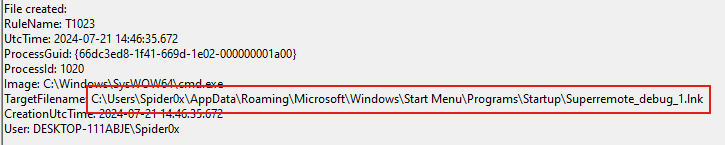
By looking at the code, we can find that it’s a code for a legitimate backup tool called “iTop”
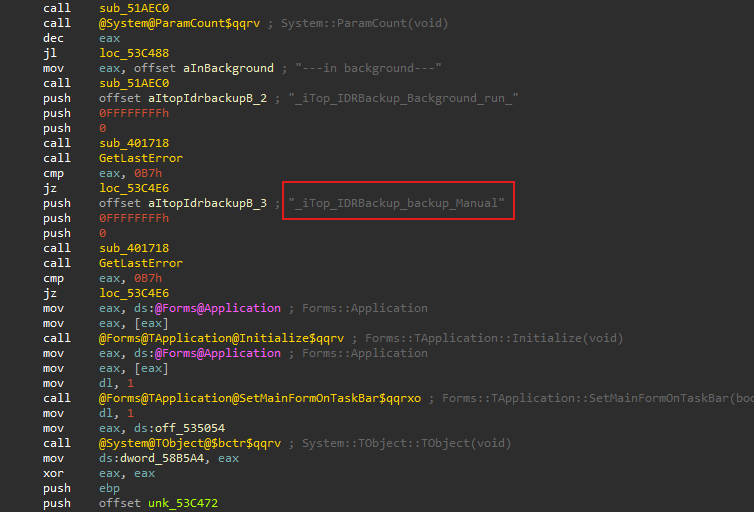
But when correlating the functionalities we found before in behavioral analysis with the code, we can find that there is an injected code before the normal app functionality starts, even before the “start” function.
This happens from the loaded modules at link time, which are the files that come with the malware.
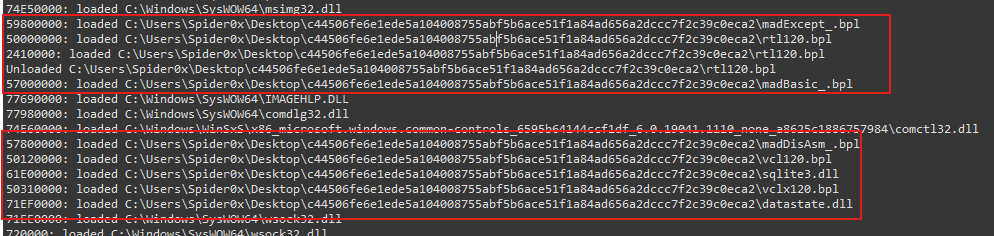
So, we can understand that the malicious functionality comes from the DLL shipped with the executable, not the executable itself.
By observing the provided DLLs, we can find one of them is more interesting which is named “madbasic_.bpl”, so we can continue with it.
When looking at the “flv” file provided, we can find that it contains what looks like encrypted content as it’s not a valid “flv” file.
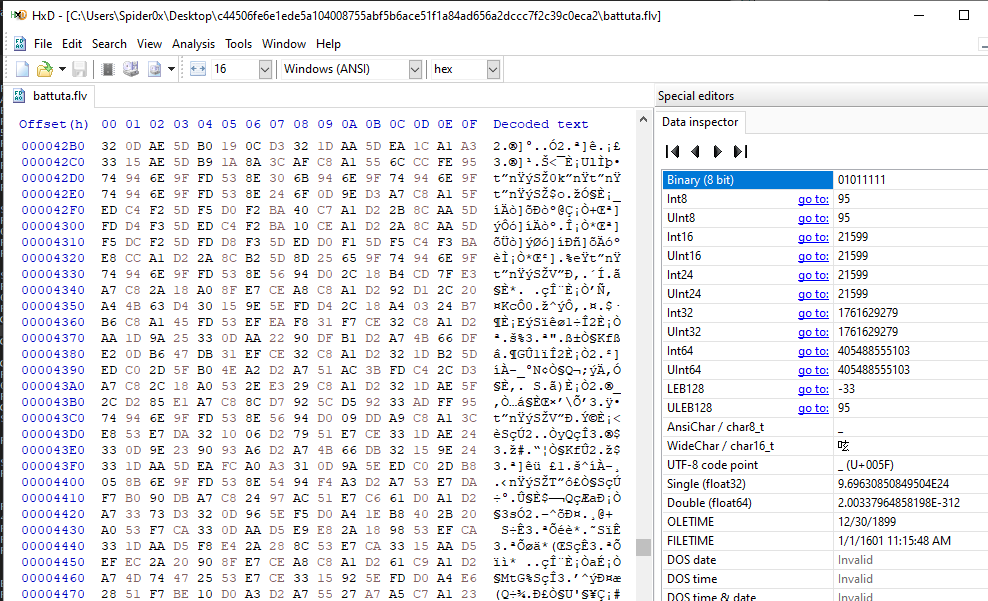
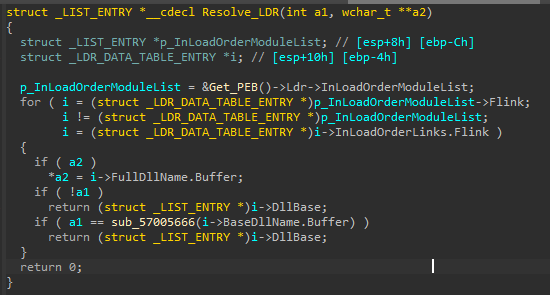
At the start, we can find the use of LDR struct to resolve Libraries dynamically.
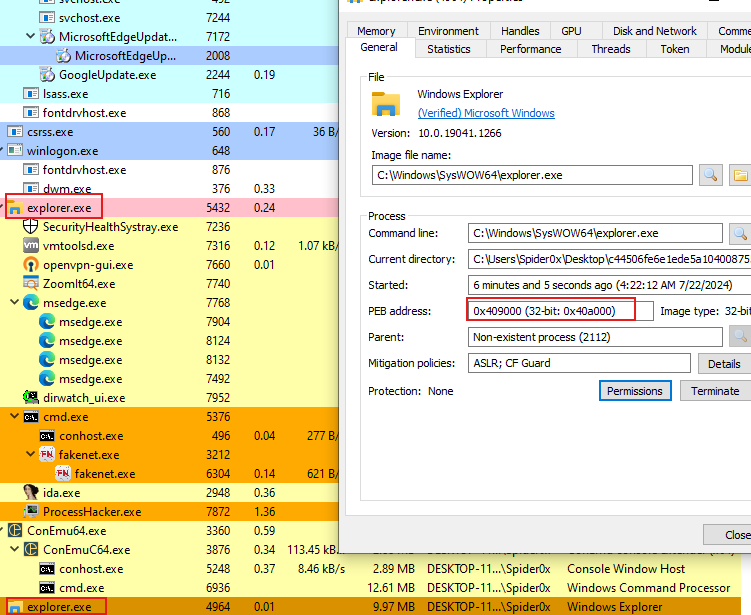
when looking at our process tree after running the malware, we can observe a second “explorer” process running as an “x32 bit” process.
So, we can get back to “Procmon” and set up a filter based on this obvious process injection technique.
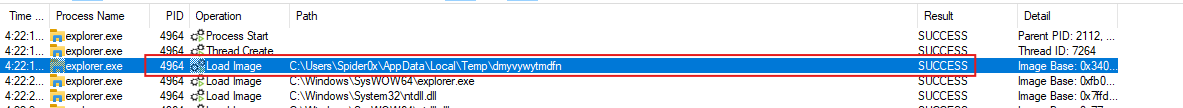
We can notice the first thing it has done is to load a DLL from the TEMP directory, which will carry the malicious activity from a legitimate explorer process.
And we can see a network connection initiated from the malicious explorer process.
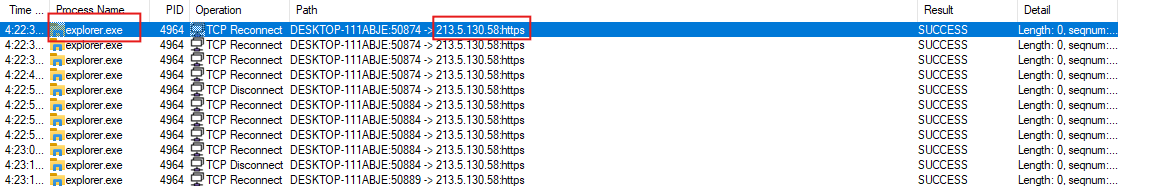
This IP as we can see is related to RamcosRAT infrastructure.
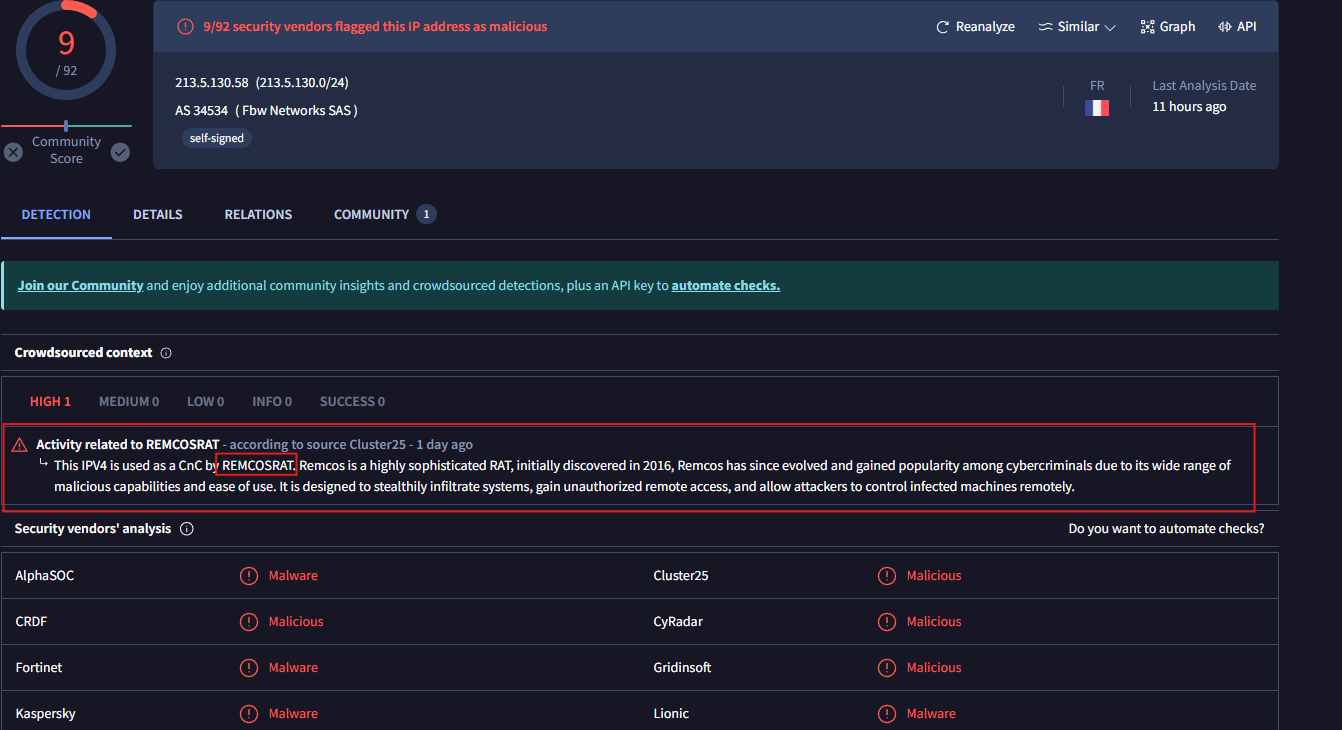
Detection
Hashs:
c44506fe6e1ede5a104008755abf5b6ace51f1a84ad656a2dccc7f2c39c0eca2
BE074196291CCF74B3C4C8BD292F92DA99EC37A25DC8AF651BD0BA3F0D020349
6010E2147A0F51A7BFA2F942A5A9EAAD9A294F463F717963B486ED3F53D305C2
4F450ABAA4DAF72D974A830B16F91DEED77BA62412804DCA41A6D42A7D8B6FD0
D6D5FF8E9DC6D2B195A6715280C2F1BA471048A7CE68D256040672B801FDA0EA
52019F47F96CA868FA4E747C3B99CBA1B7AA57317BF8EBF9FCBF09AA576FE006
835F1141ECE59C36B18E76927572D229136AEB12EFF44CB4BA98D7808257C299
931308CFE733376E19D6CD2401E27F8B2945CEC0B9C696AEBE7029EA76D45BF6
B1FCB0339B9EF4860BB1ED1E5BA0E148321BE64696AF64F3B1643D1311028CB3
5AE3838D77C2102766538F783D0A4B4205E7D2CDBA4E0AD2AB332DC8AB32FEA9
02F37A8E3D1790AC90C04BC50DE73CD1A93E27CAF833A1E1211B9CC6294ECEE5
B6F321A48812DC922B26953020C9A60949EC429A921033CFAF1E9F7D088EE628
2BDF023C439010CE0A786EC75D943A80A8F01363712BBF69AFC29D3E2B5306ED
IPs
213.5.130.58
Sigma Hunting
title: Detect Windows Defender Exclusions Added via PowerShell
status: experimental
description: Detects when exclusions are added to Windows Defender using PowerShell.
author: Amr Ashraf
date: 2024/07/21
logsource:
product: windows
service: sysmon
definition: 'Requirements: Sysmon with a configuration that includes event ID 1 (process creation)'
detection:
selection:
EventID: 1
CommandLine|contains:
- "powershell"
- "Add-MpPreference"
- "Set-MpPreference"
condition: all of selection
fields:
- User
- Image
- CommandLine
- ParentImage
falsepositives:
- Legitimate administrative changes to Windows Defender configuration
level: high
tags:
- attack.defense_evasion
title: Detect Dropping LNK File into Startup Folder
status: experimental
description: Detects when a .lnk file is dropped into the Windows Startup folder, a common persistence technique.
author: Amr Ashraf
date: 2024/07/21
logsource:
product: windows
service: sysmon
definition: 'Requirements: Sysmon with a configuration that includes event ID 11 (file creation)'
detection:
selection:
EventID: 11
TargetFilename|endswith:
- '.lnk'
TargetFilename|contains|all:
- '\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\'
condition: all of selection
fields:
- TargetFilename
- Image
- User
- Hashes
falsepositives:
- Legitimate software installations that place shortcuts in the Startup folder
- User-created shortcuts for legitimate purposes
level: high
tags:
- attack.persistence