AveMariaRAT Analysis
INFO
“Ave Maria” is a RAT (Remote Access Trojan), also known as WARZONE RAT. It offers a wide range of features, such as stealing victims’ sensitive information and remote controlling an infected device, including privilege escalation, remote desktop control, camera capturing, and more.
Packed Sample hashes:
- md5 80158B31173F6E2BC97D5AD1FA9E365F
- sha1 55DD7F373C8124EB14B85BD695037B1785F9EA57
- sha256 29FF714C2F514B551EC5104304AD932BBFBEE019A818E7662A572E19690FC2C6
Manual Unpacking
This sample is packed as it has a high value of entropy as shown below
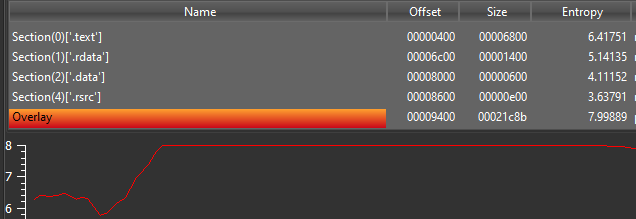
At the start, we will notice that the file has no ‘main’ function as all the code is inside the ‘start’ function directly So I started analyzing from there, passing the part of loading some libraries and initializing the environment and getting the command line arguments that will be generated by the compiler, we will start to find that the file starts to get the ‘TEMP’ file path
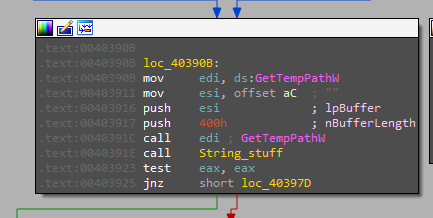
And opens a handle to itself and a file in the temp directory decrypts the second stage and writes it to an executable and other different files in the TEMP directory, in our case “efwhixxln.exe”.
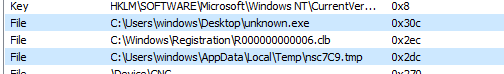
Then execute it with an argument to another downloaded file in the TEMP directory “ozirvdg.dl”
Second Stage
- sha256 38D21B3DFE90616A23D9D63775C9C99CA23D79A072D48CEF0A5749F4A7AF4DC4
At the very start here is a big welcome from our sample with this small anti-analysis technique, where it uses the time it took from the CPU to execute specific instructions and based on the fact that the debugger will make the execution take more time than the malware catches the debugger.
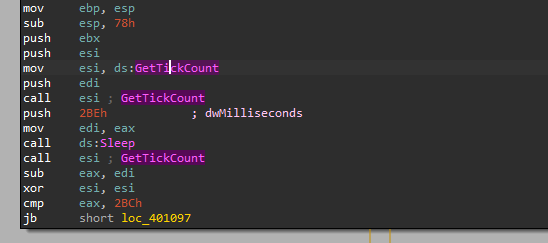
The file passed on the argument on start is read to the memory followed by an allocation to a big memory with ‘RWX’ permissions.
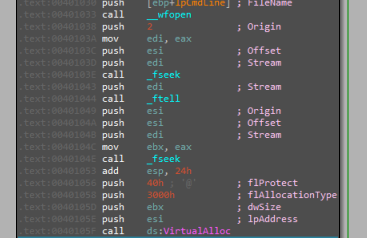
then decrypting the content of the file with a simple XOR operation with the key “32h” and transferring the execution there.
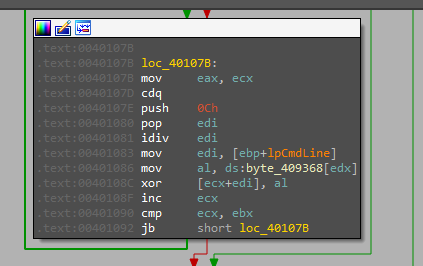
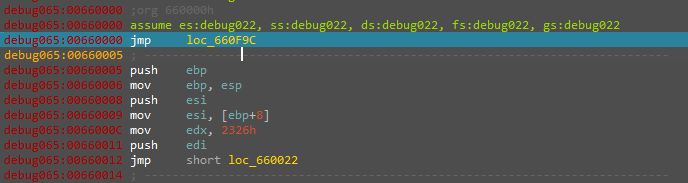
The decrypted payload starts with resolving the libraries using the ‘LDR’ structure in the PEB and resolving the APIs with their hash
The details of the method described before in previous analysis on my blog:
Enumerate loaded modules using LDR Structure
The file then allocates a very big junk of memory zeros it out and frees it again “delay mechanism” and start dealing with another file created in the TEMP directory during the first stage.
Creates a directory in “AppData\Roaming” and moves itself there and adds an entry to the “Run” key
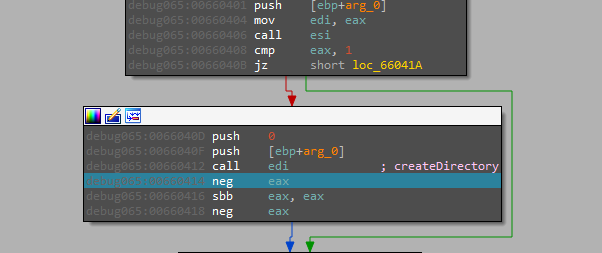
the file that dropped from the first stage is read and decrypted and another instance of itself gets created as a child process in a suspended state.
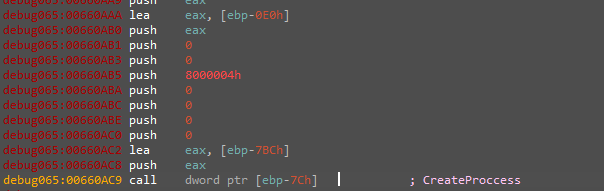
It will then open “ntdll.dll” and copy it to its memory which is a technique used to bypass hooking as it makes its own copy of it. So why is that?!
There are a lot of techniques used to bypass hooking by AVs in the userland, the technique used here is doing the following, instead of calling a function inside “ntdll.dll” which may be hooked why not doing the job it’s doing for us by our selves, so we first need to understand what it’s doing for us to replace that in our code. “NTDll.dll” is used just to replace the function that needs to be executed by the user simply to just a number passed to a call to instruction named “syscall”, so the malware copy the dll to its memory and parses it to extract those numbers and passing them by itself to the “syscall”.
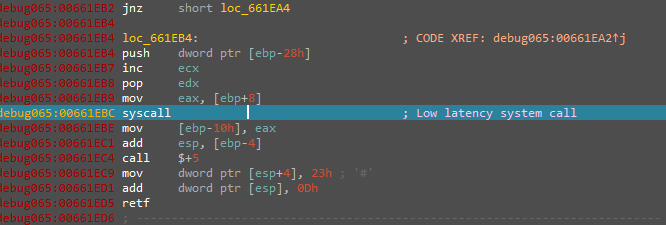
Using this way the malware resumes the thread inside the created process to start executing the decrypted code which is the actual sample that will be our RAT.
Stage 3 (AveMariaRAT)
Proxy config
Starting with adding a new entry to the key “Software\Microsoft\Windows\CurrentVersion\Internet Settings” which is responsible for configuring the local proxy.
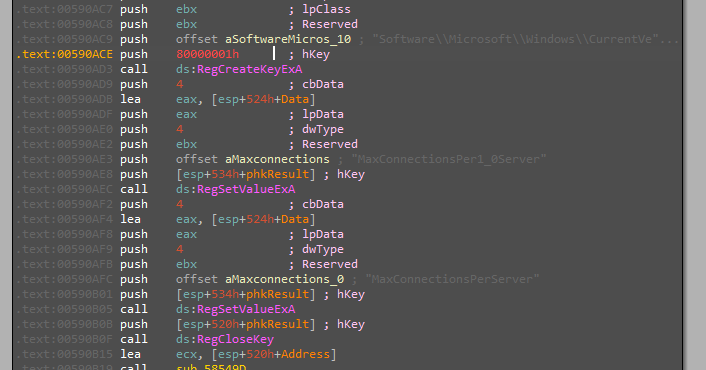
There is a folder then created called “Microsoft Vision”
C2 Server
Then the malware tries to reach out for its C2 “193.42.33.225” which appears to be down at the time of analysis.
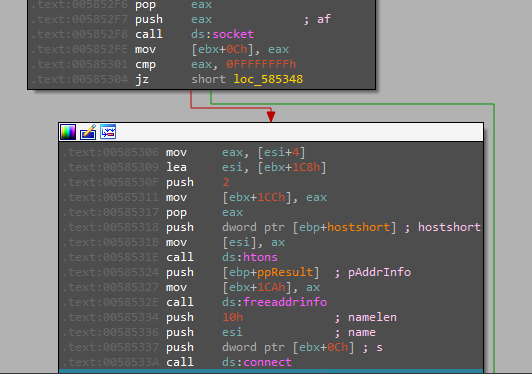
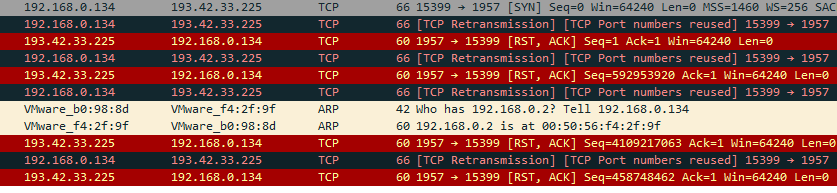
But once the Connection is done with the C2, the machine is ready to receive the commands and execute them in the machine.
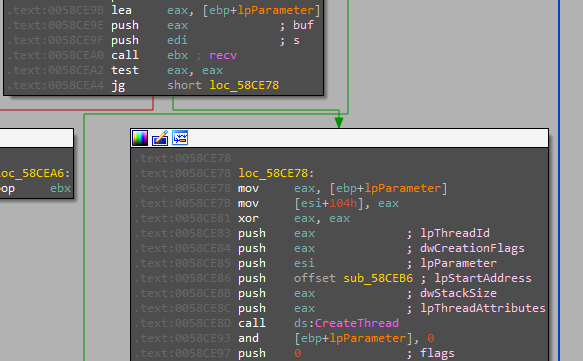
The command received from the server is then interpreted by this function.
Privilege escalation
The malware is doing privilege escalation using a separate executable saved in the resources section.
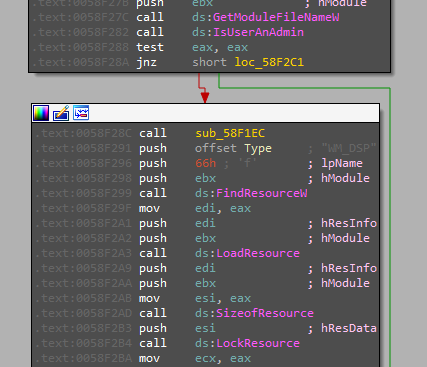
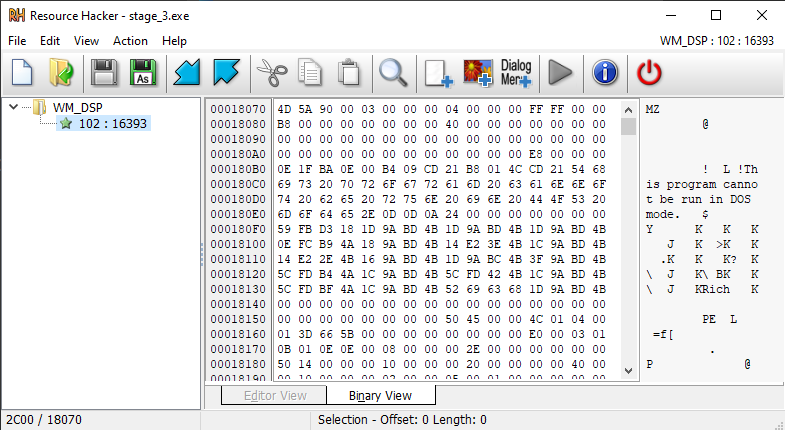
Short speaking AveMaria has 2 UAC bypass techniques, and one of them is abusing the DLL Hijacking vulnerability of Dism.exe. This feature uses malware saved with the name WM_DSP in the resource section and abuses the fact the key is HKCU registry key that Auto Elevate program can modify without admin permission.
CMD
AveMaria can pipe the result of “cmd.exe” to the socket connection.
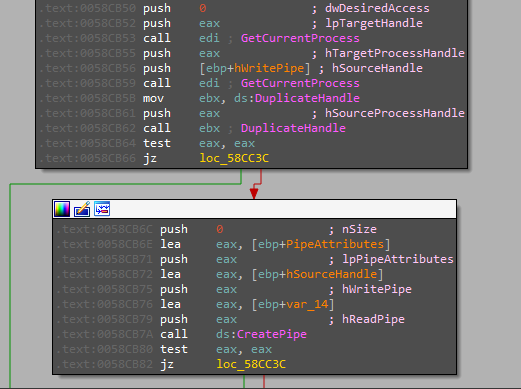
Keylogging
AveMaria has the ability also to act as a key logger.
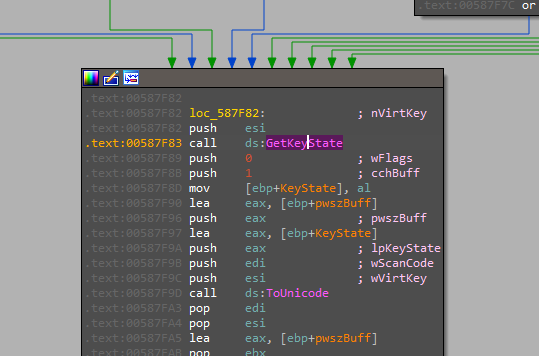
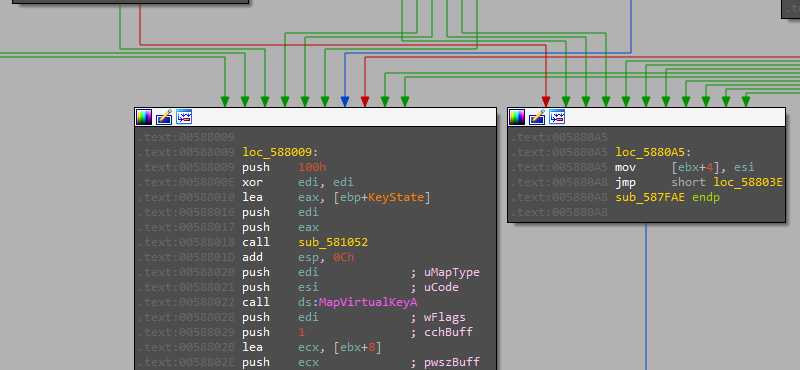
and here is the switch statement for the keylogging
The logged strokes are named with the time and saved to the previously mentioned folder “Microsoft Vision”
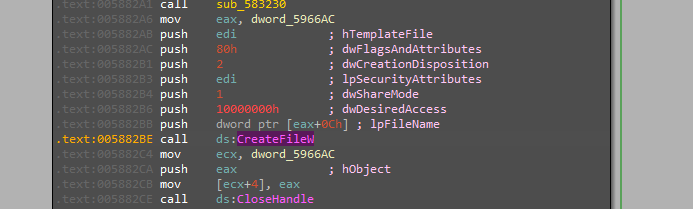
Persistance
In addition to the “run” method mentioned before, AvMaria also has the ability to accomplish persistence by adding a service.
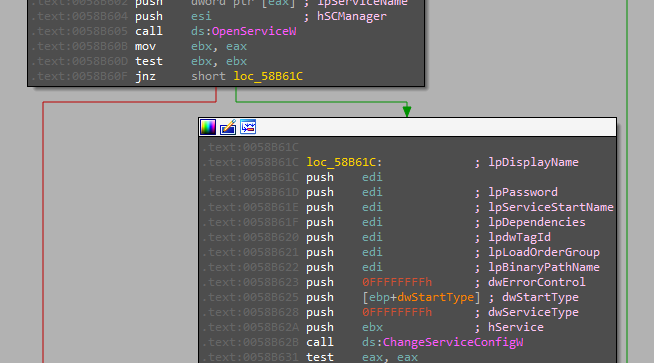
Info Stealer
AvMaria also has the capability of Info stealers built in.
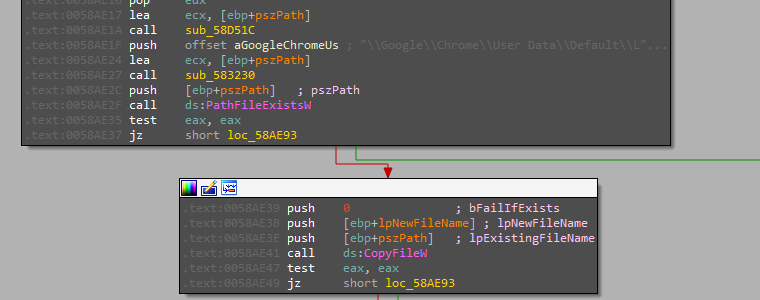
here is a list of enumerated data:
- Chrome Browser
- Internet explorer Browser
- firefox Browser
- Email clients “outlook”…
- RDP Clients “RDPClip”