Splunk Investigation
Description
BOTSv1 is a real world cyberdefenders ctf. It uses Splunk as a SIEM tool to use it in threat hunting.
Reconnaissane
The name of the company website is “imreallynotbatman.com”
staring search with the filter “index=”botsv1” imreallynotbatman.com”
still, there is a lot of events related to that website so we should narrow our search by adding a filter to choose the stream of data we need to look at.
using the filter “index=”botsv1” imreallynotbatman.com sourcetype=”stream:http”” we choosed http stream as our source tybe. by scrooling abit we will notise the use of “Acunetix Web Vulnerability Scanner”
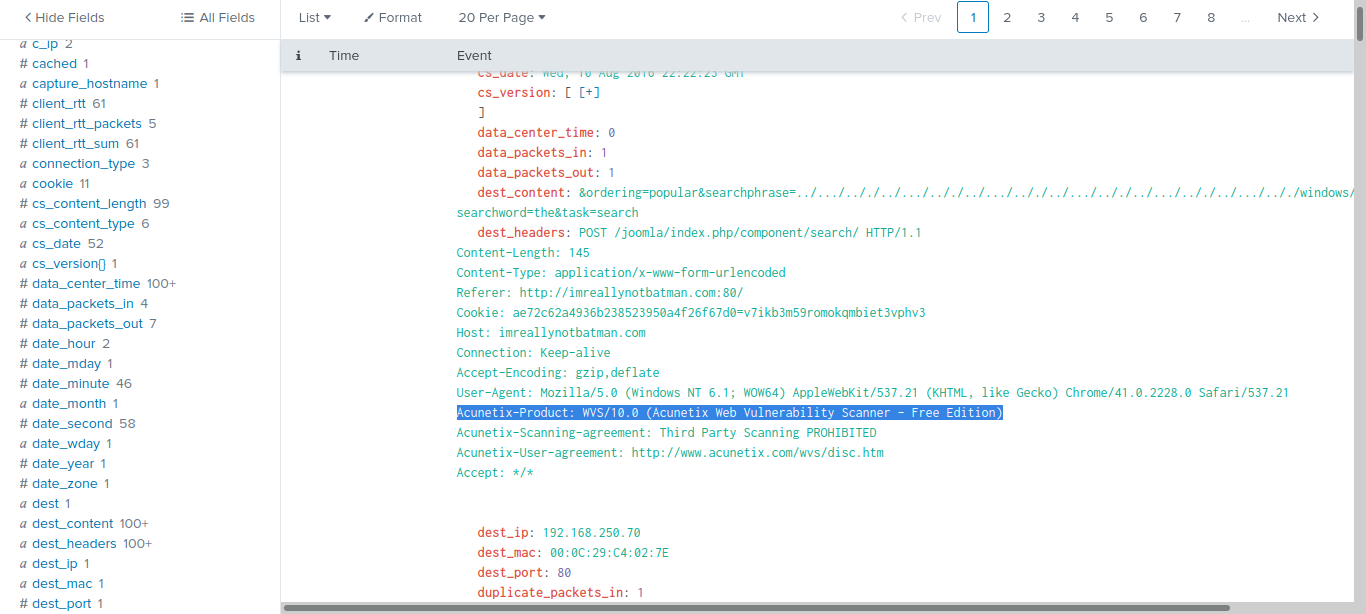
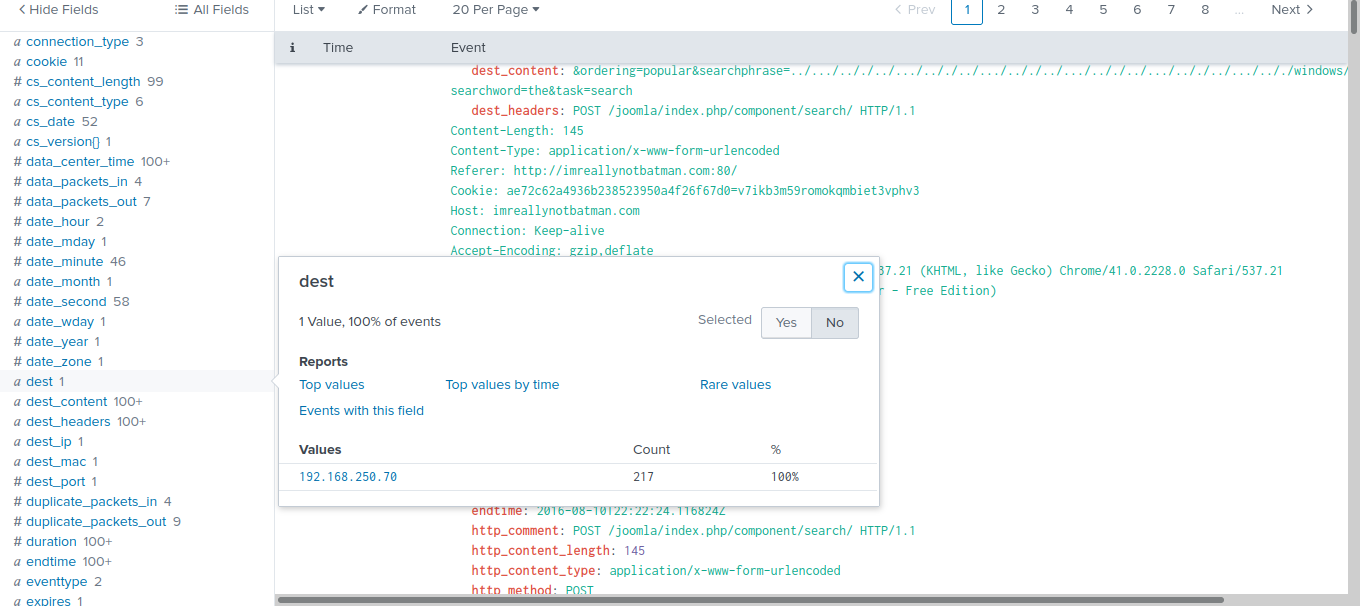
now we need to know the IP address which the scanner is scanning. we can do that by going to the “dest” which will show us that the IP is “192.168.250.70”.
now we need the attacker IP which is clearly will be obvious by applying the “src_ip” filter
due to high traffic generated by the scanner.
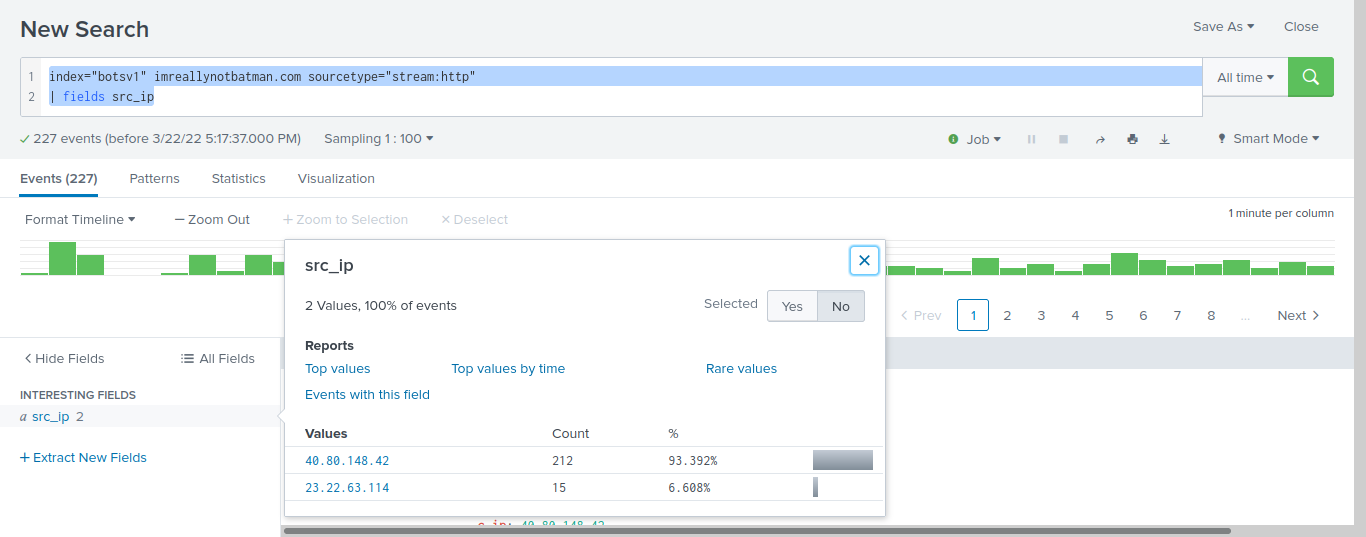
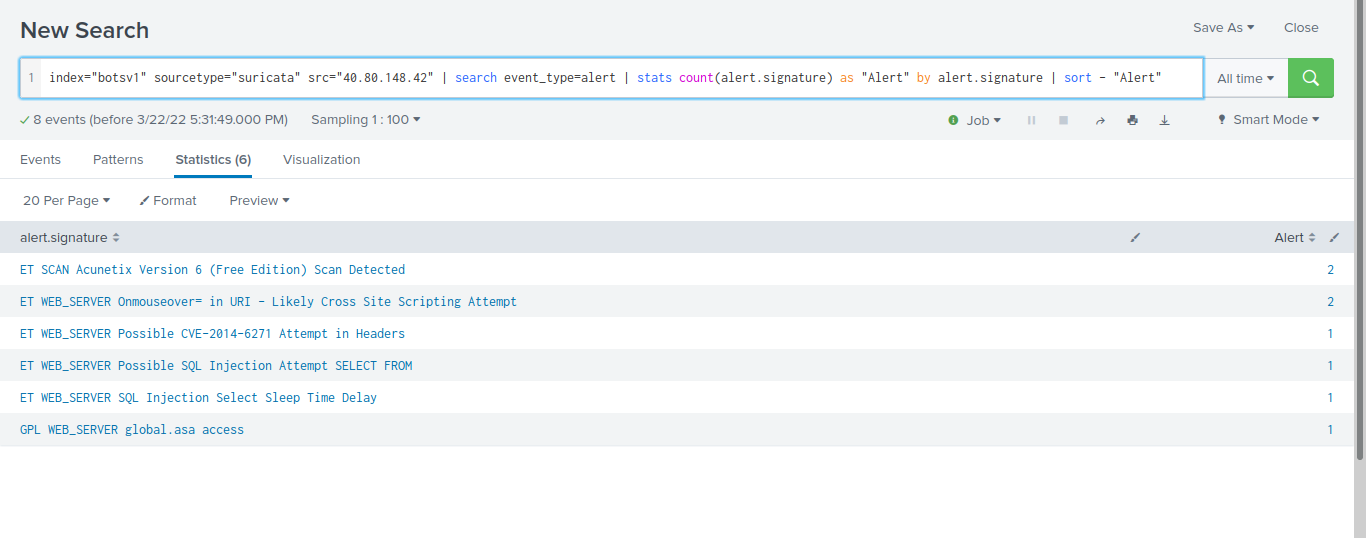
now we have the attackers ip so we can search the surcata type source for the alarts created by that ip with the command
"index="botsv1" sourcetype="suricata" src="40.80.148.42" | search event_type=alert | stats count(alert.signature) as "Alert" by alert.signature | sort - "Alert""
we can also filter the uri which scanned by using the command
"index="botsv1" sourcetype="stream:http" status=200 src="40.80.148.42" dest="192.168.250.70" | stats count by uri | sort - count"
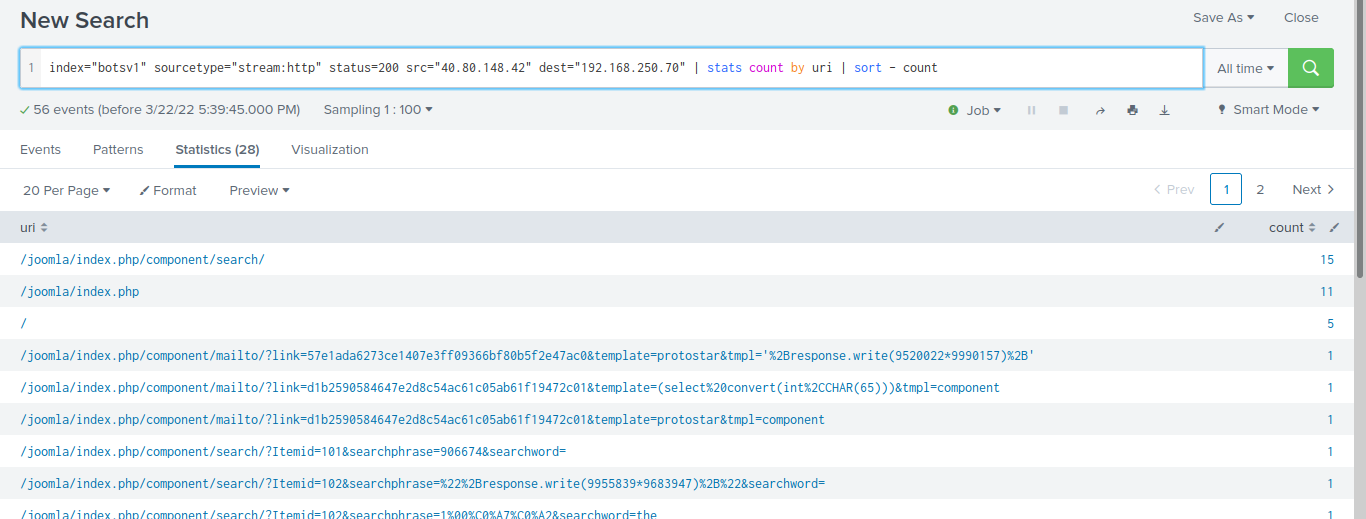
from the output, it is clear that the attacker tries to scan Joomla site.
Delivery activity
in this phase, we use threat intelligence to gather information with previously collected data to search for adversaries. first, we can use the IP “ 23.22.63.114” which we found from the logs to search for known malware or apt uses this IP.
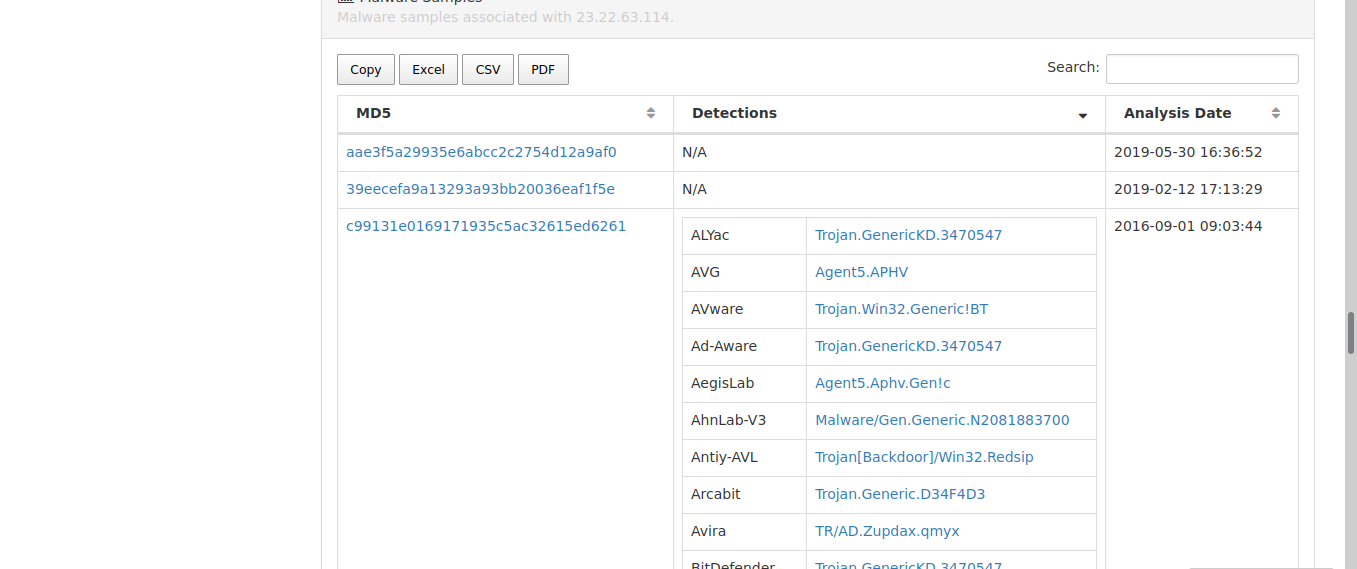
if we submit MD5 hashes to open sources such as VirusTotal or Hybrid Analysis, we can retrieve metadata about those samples, which is useful in future investigations.
Exploitation activity
In this phase, we’ll employ Splunk to uncover any exploitation activity on the network. Let’s us focus on stream:http sourcetype. The query is: “Index=botsv1 sourcetype=”stream:http”” then choosing http method to be “post”
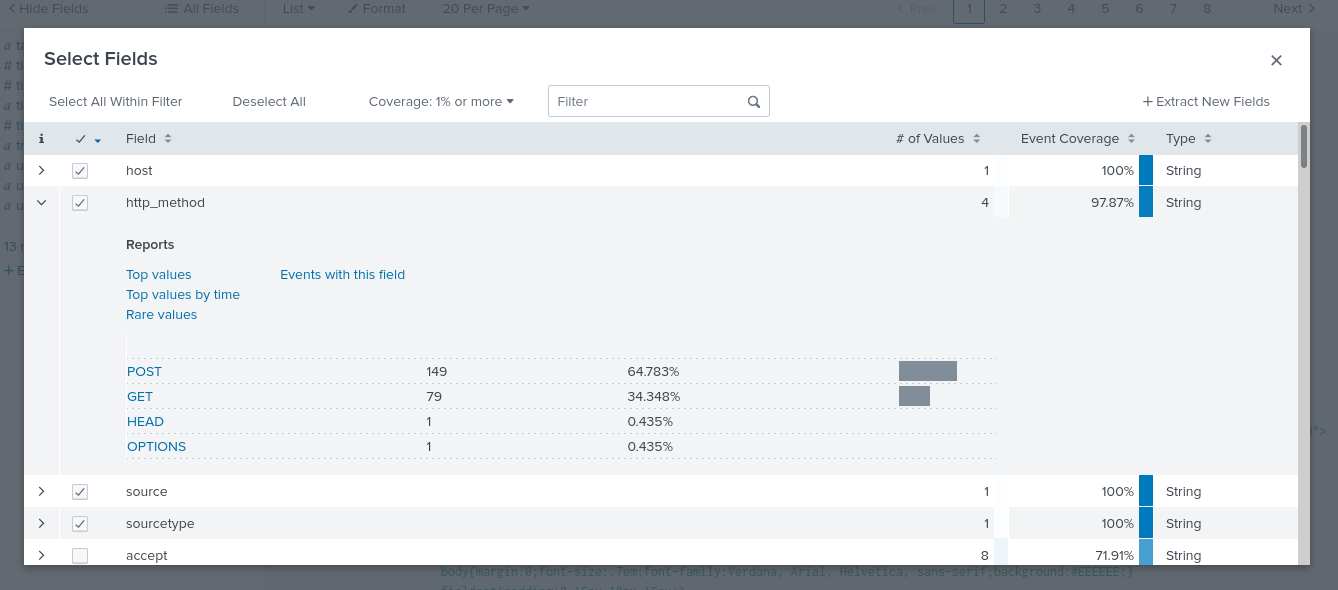
We are also interested in the requests being sent to 192.168.250.70, which is our organization’s website. The search we use is as the following.
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix"
Note: NOT “Acunetix” is specified to exclude Acunetix scanner requests.
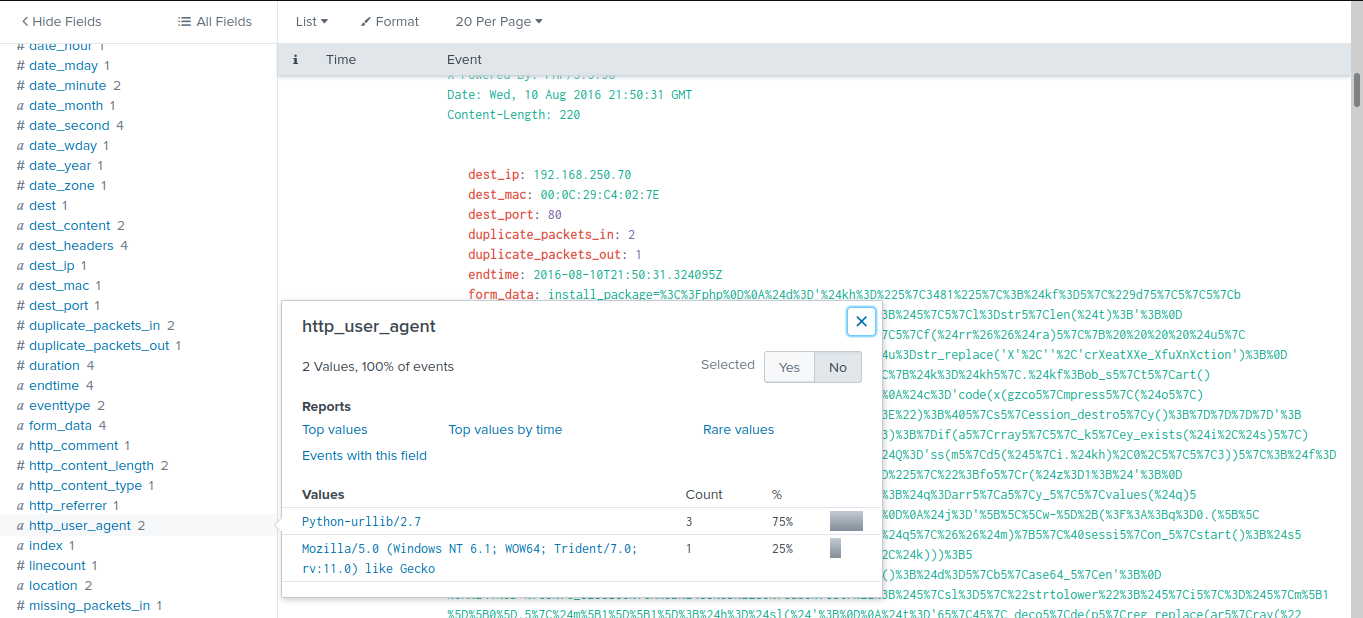
looking at the user agent field we see python script is used so let’s include it in our filter “index=”botsv1” sourcetype=”stream:http” http_method=”POST” dest=”192.168.250.70” NOT “Acunetix” http_user_agent=”Python*””
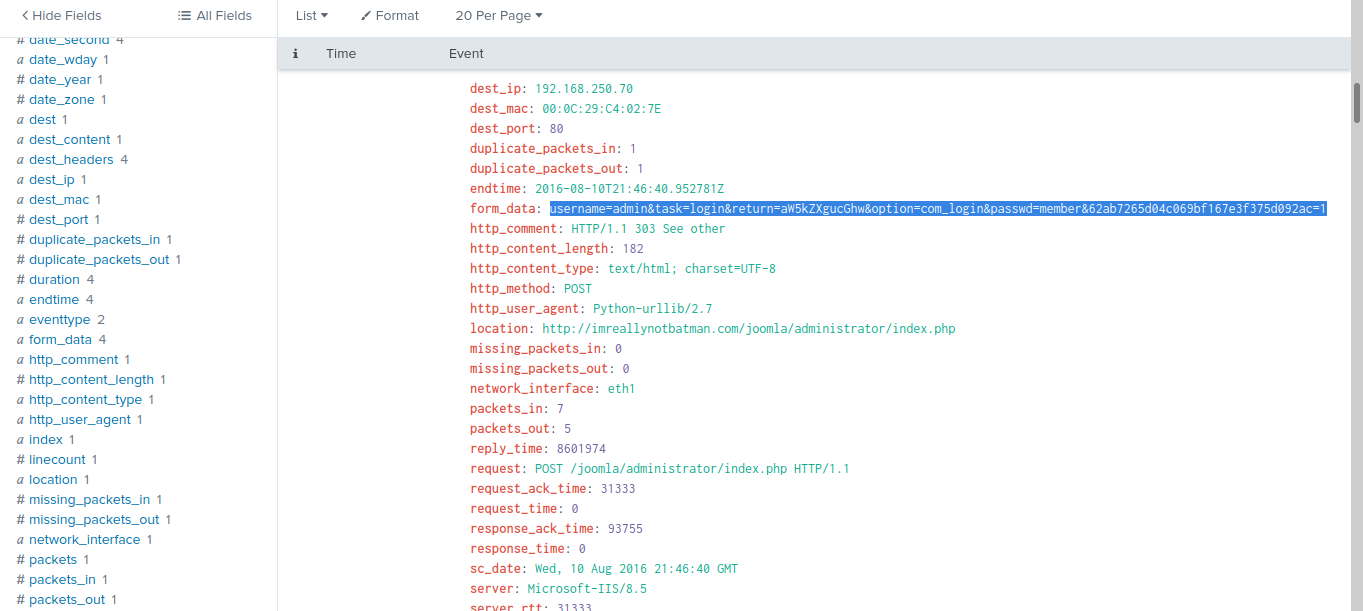
Scroll down a little bit, we can see that the form_data contains values of username and password! Considering the below query:
"index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix" http_user_agent="Python*" | table _time,form_data,c_ip | sort + _time"
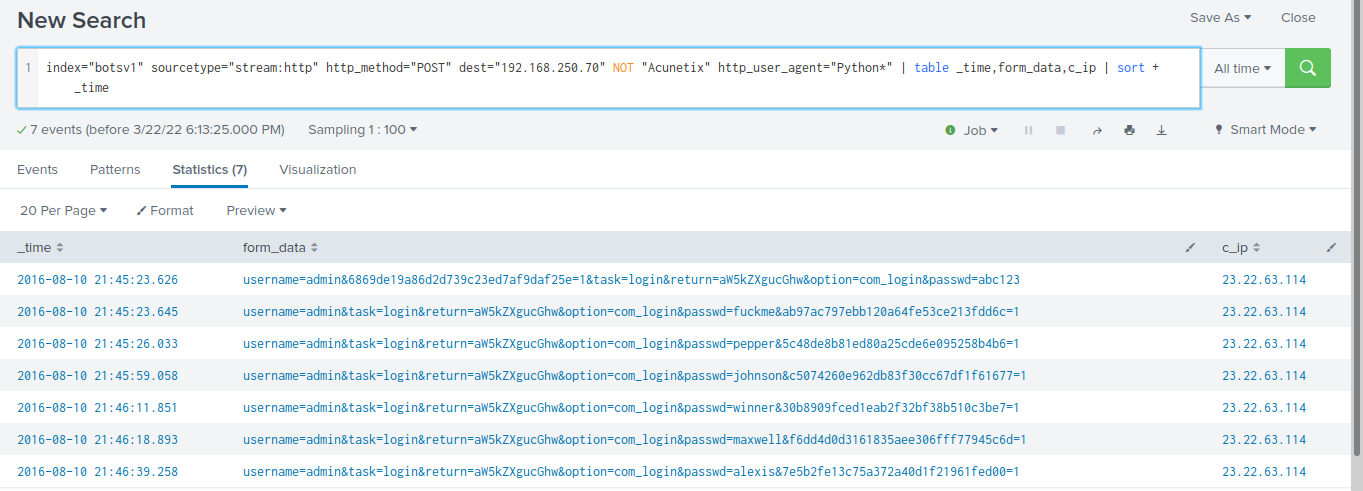
It’s undoubtedly that the APT performed password brute-forcing.